
Solving the Top Five PAM Challenges of Identity Teams

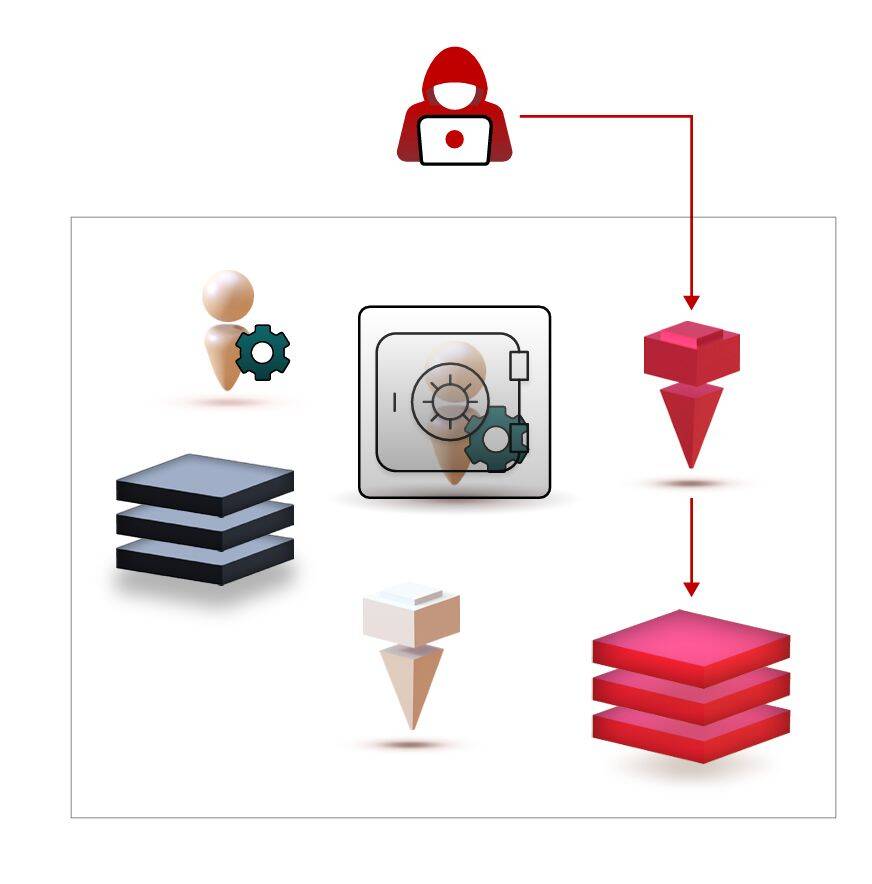
While many of the privileged accounts in the environment do gain PAM protection, there are those that don’t.
For some of them, it’s a temporary, yet dangerously lingering, state that results from the length of the PAM onboarding journey, that can take months and even years. While these accounts are planned to onboard the PAM solution, they are exposed to compromise in the meantime.
Other privileged accounts are deemed to a permanent residence outside of the PAM protection. The most prominent examples of these are service accounts with complex and hard-to-map dependencies. Often, identity teams would rather take the risk of these accounts getting compromised than the certainty of breaking the critical processes these accounts manage, as a result from password rotation. In both cases, the result is the same – privileged accounts that are exposed to compromise.
Securing accounts that can’t be vaulted
PAM Challenge #5: You Can’t Protect What’s Not There

Solving the Top Five PAM Challenges of Identity Teams

85%
Nullam placerat, nulla ac ultricies euismod, mauris lacus gravida leo, id convallis justo massa eu urna.
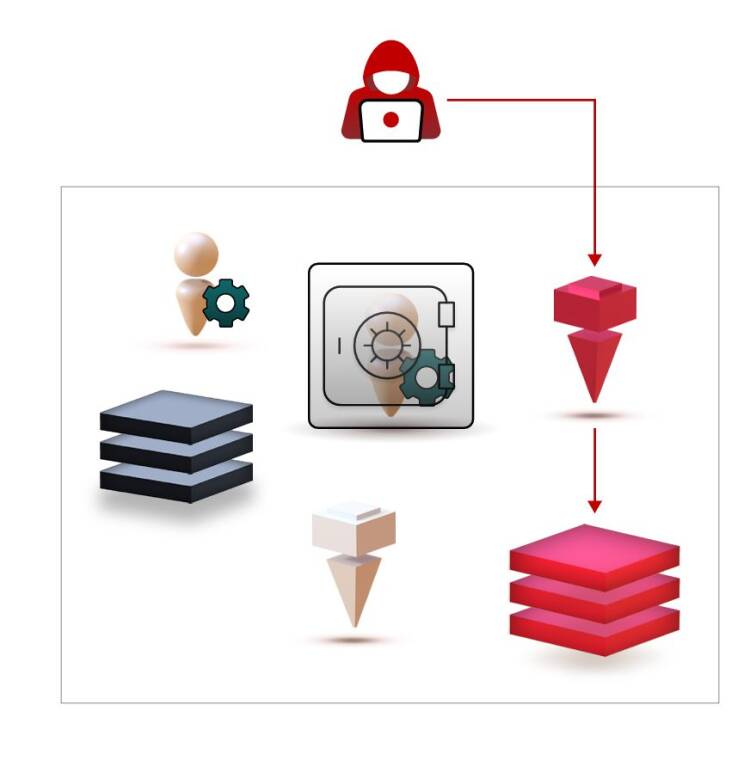
While many of the privileged accounts in the environment do gain PAM protection, there are those that don’t.
For some of them, it’s a temporary, yet dangerously lingering, state that results from the length of the PAM onboarding journey, that can take months and even years. While these accounts are planned to onboard the PAM solution, they are exposed to compromise in the meantime.
Other privileged accounts are deemed to a permanent residence outside of the PAM protection. The most prominent examples of these are service accounts with complex and hard-to-map dependencies. Often, identity teams would rather take the risk of these accounts getting compromised than the certainty of breaking the critical processes these accounts manage, as a result from password rotation. In both cases, the result is the same – privileged accounts that are exposed to compromise.
PAM Challenge #5: You Can’t Protect What’s Not There