
Solving the Top Five PAM Challenges of Identity Teams

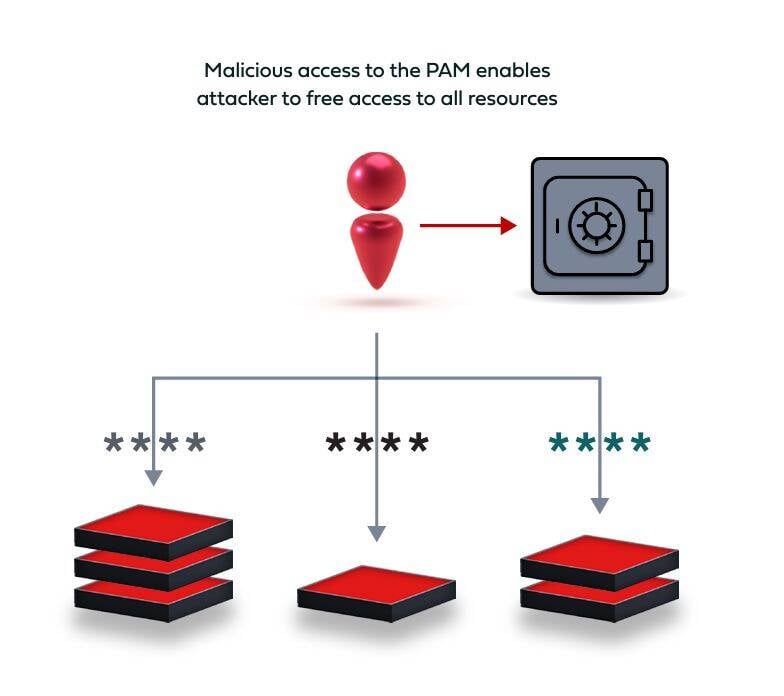
T he inherent downside of every security solution is that if it falls prey to an adversary, the potential damage is huge. While the PAM solution guards all privileged access to the organization’s resources, it can’t do the same for accessing itself.
There are various access interfaces for a PAM solution: the web portal that is used for credential retrieval as well as administrative tasks; Proxy Access – used by system administrators to connect to systems using vaulted credentials (this is the preferred method by system administrators as it is more transparent); and API Access – used for automated tasks and service accounts.
An adversary that manages to compromise the credentials of one of the PAM admins can gain the full trove of privileged access capabilities to practically any resource within the environment.
Protecting access to the PAM itself
PAM Challenge #4: You Can’t Use a Protector to Protect Itself

Solving the Top Five PAM Challenges of Identity Teams

85%
Nullam placerat, nulla ac ultricies euismod, mauris lacus gravida leo, id convallis justo massa eu urna.
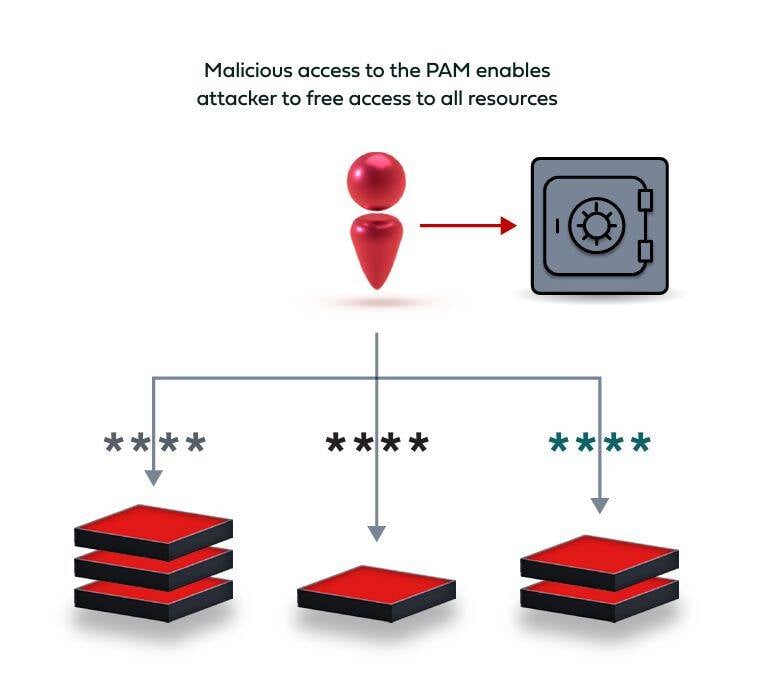
T he inherent downside of every security solution is that if it falls prey to an adversary, the potential damage is huge. While the PAM solution guards all privileged access to the organization’s resources, it can’t do the same for accessing itself.
There are various access interfaces for a PAM solution: the web portal that is used for credential retrieval as well as administrative tasks; Proxy Access – used by system administrators to connect to systems using vaulted credentials (this is the preferred method by system administrators as it is more transparent); and API Access – used for automated tasks and service accounts.
An adversary that manages to compromise the credentials of one of the PAM admins can gain the full trove of privileged access capabilities to practically any resource within the environment.
PAM Challenge #4: You Can’t Use a Protector to Protect Itself