
Solving the Top Five PAM Challenges of Identity Teams

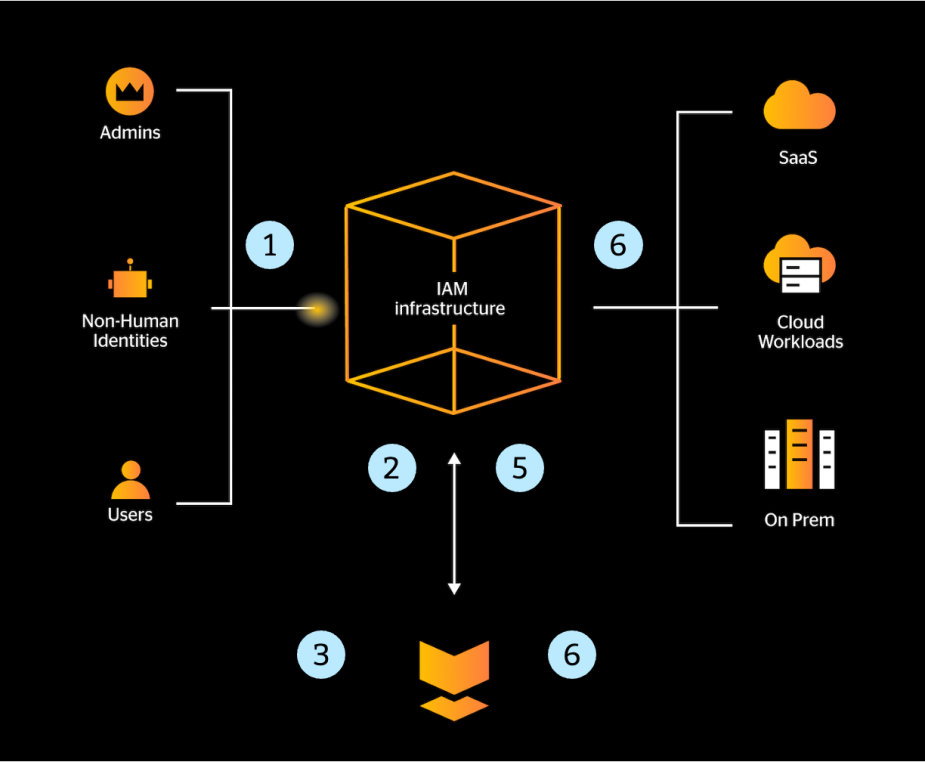
The core of the Unified Identity Protection platform is its integration with the IDP. With this integration, the platform becomes a native part of the authentication flow in the following manner:
A user initiates an access request to an on-prem or cloud resource.
The respective IDP forwards the access request to Silverfort for analysis.
Silverfort analyzes the access request and determines whether toallow access, block it, or challenge the user with MFA.
If an MFA is required, Silverfort instructs an MFA service to send theuser an MFA message and pass the user response back to Silverfort.
Based on the response, Silverfort passes its verdict to the IDP.
The IDP grants or denies the user access to the resource, based on Silverfort verdict.
How Does an Identity Security Platform Work?

Solving the Top Five PAM Challenges of Identity Teams

85%
Nullam placerat, nulla ac ultricies euismod, mauris lacus gravida leo, id convallis justo massa eu urna.
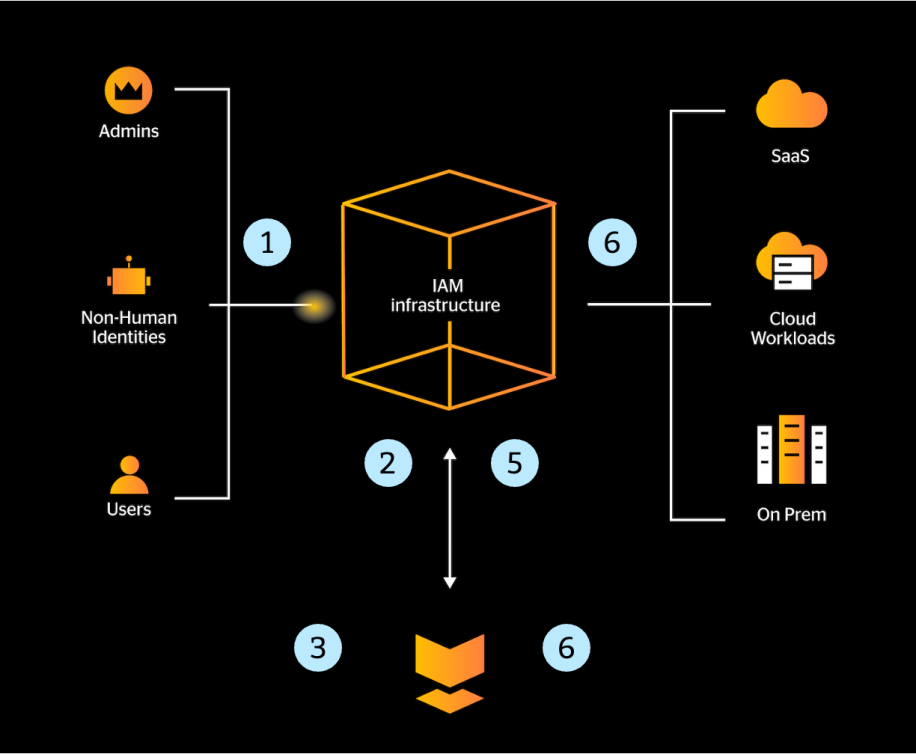
The core of the Unified Identity Protection platform is its integration with the IDP. With this integration, the platform becomes a native part of the authentication flow in the following manner:
A user initiates an access request to an on-prem or cloud resource.
The respective IDP forwards the access request to Silverfort for analysis.
Silverfort analyzes the access request and determines whether toallow access, block it, or challenge the user with MFA.
If an MFA is required, Silverfort instructs an MFA service to send theuser an MFA message and pass the user response back to Silverfort.
Based on the response, Silverfort passes its verdict to the IDP.
The IDP grants or denies the user access to the resource, based on Silverfort verdict.
How Does an Identity Security Platform Work?