
Solving the Top Five PAM Challenges of Identity Teams

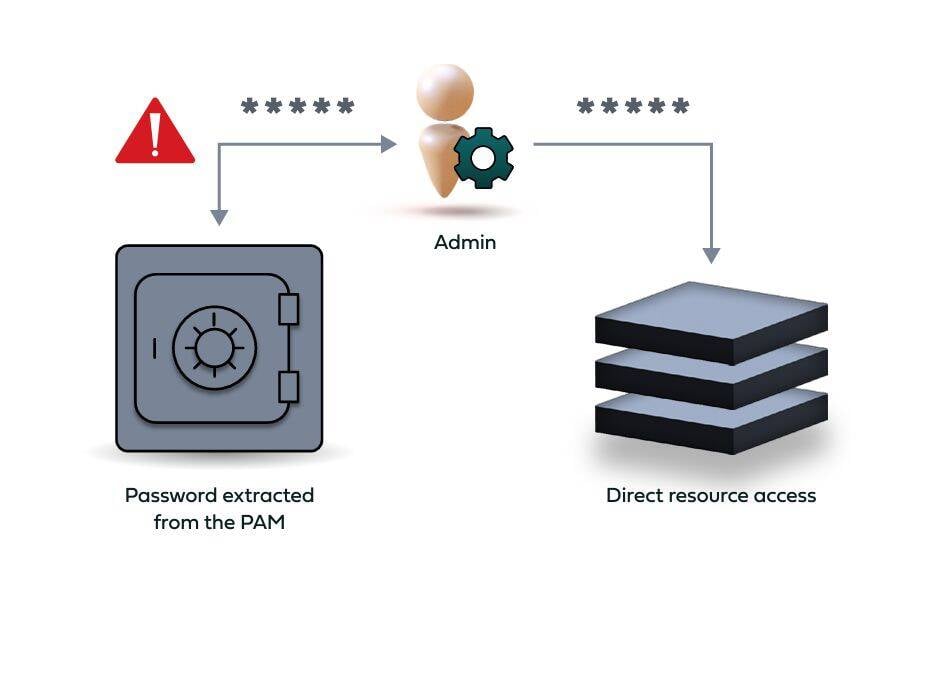
As a rule of thumb, even the best security technology is as strong – or weak – as the person that operates it. PAM is designed and built to protect admin accounts from compromise with various measures such as password rotation, vaulting, session recording and others. However, it often results with some degree of downgrade in the admins’ login user experience. As a result, there is a common malpractice among admins to log into the PAM box, extract their newly generated password and log in directly to the servers and workstations they need, bypassing the PAM altogether.
Needless to say, such a scenario voids the PAM protection for these accounts altogether. Unfortunately, the PAM itself cannot prevent this practice from taking place, leaving a critical, unattended security gap..
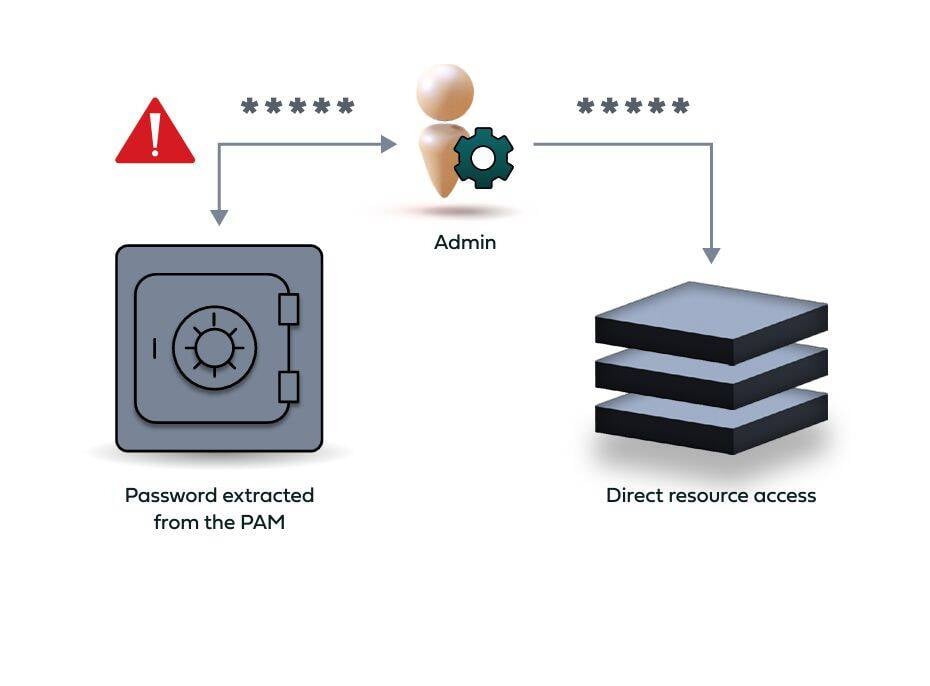
Admins that deliberately bypass the PAM
PAM Challenge #3: You Can’t Defend Those Who Refuse to be Defended

Solving the Top Five PAM Challenges of Identity Teams

85%
Nullam placerat, nulla ac ultricies euismod, mauris lacus gravida leo, id convallis justo massa eu urna.
As a rule of thumb, even the best security technology is as strong – or weak – as the person that operates it. PAM is designed and built to protect admin accounts from compromise with various measures such as password rotation, vaulting, session recording and others. However, it often results with some degree of downgrade in the admins’ login user experience. As a result, there is a common malpractice among admins to log into the PAM box, extract their newly generated password and log in directly to the servers and workstations they need, bypassing the PAM altogether.
Needless to say, such a scenario voids the PAM protection for these accounts altogether. Unfortunately, the PAM itself cannot prevent this practice from taking place, leaving a critical, unattended security gap..
PAM Challenge #3: You Can’t Defend Those Who Refuse to be Defended