
Re-evaluate your MFA: Are You as Protected as You Should Be?

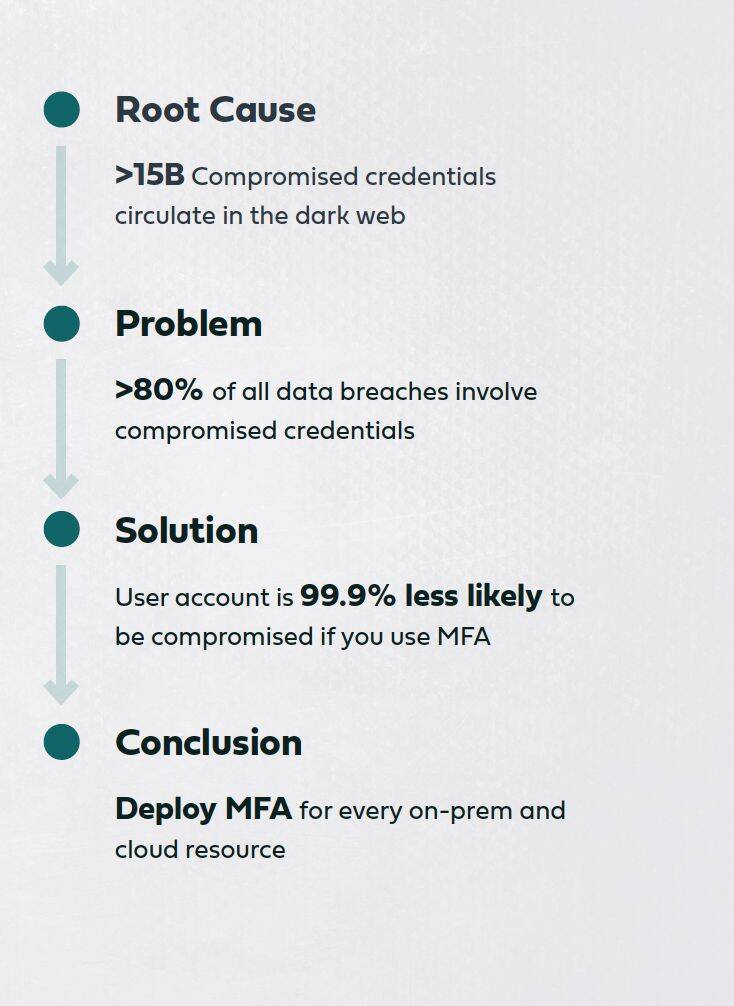
Identity-based attacks that utilize compromised credentials to access targeted resources are gaining momentum as the #1 cause of data breaches across both on-prem and cloud resources. MFA is the ultimate, proven solution to block such attacks. This leads to the inevitable conclusion that every resource that is accessed with credentials must be subject to MFA protection.
The problem, however, is that truly comprehensive MFA protection – one that covers all network assets - has been exceedingly difficult to achieve, and often isn’t even attempted because it does not seem possible.
Why is MFA more important than ever?

Re-evaluate your MFA: Are You as Protected as You Should Be?

85%
Nullam placerat, nulla ac ultricies euismod, mauris lacus gravida leo, id convallis justo massa eu urna.
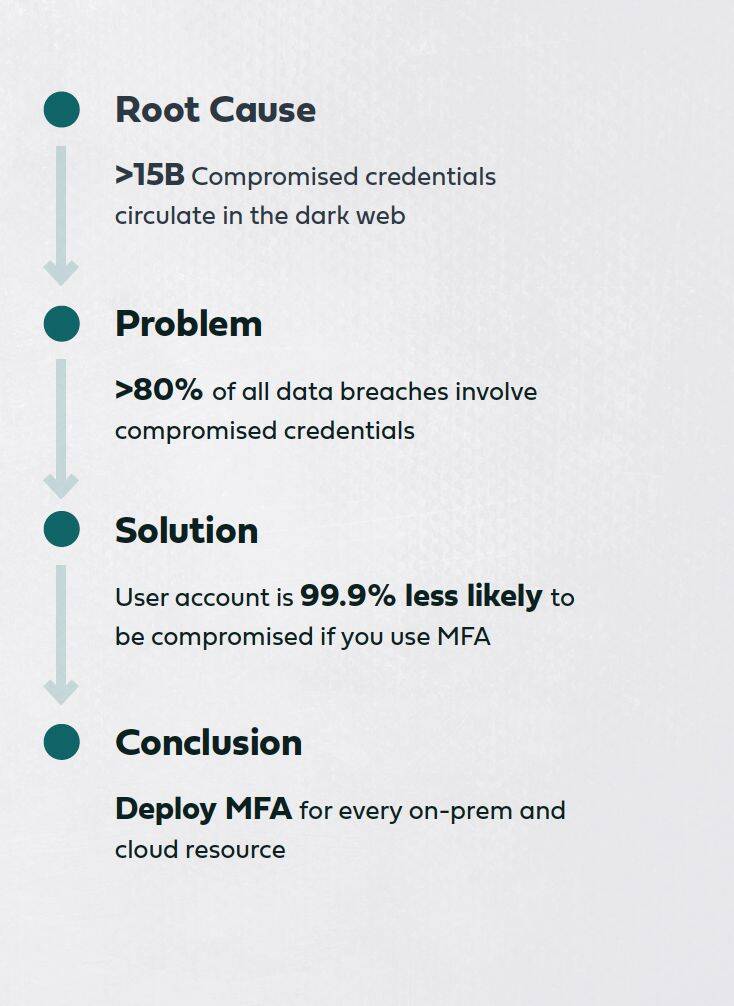
Identity-based attacks that utilize compromised credentials to access targeted resources are gaining momentum as the #1 cause of data breaches across both on-prem and cloud resources. MFA is the ultimate, proven solution to block such attacks. This leads to the inevitable conclusion that every resource that is accessed with credentials must be subject to MFA protection.
The problem, however, is that truly comprehensive MFA protection – one that covers all network assets - has been exceedingly difficult to achieve, and often isn’t even attempted because it does not seem possible.
Why is MFA more important than ever?