
Re-evaluate your MFA: Are You as Protected as You Should Be?

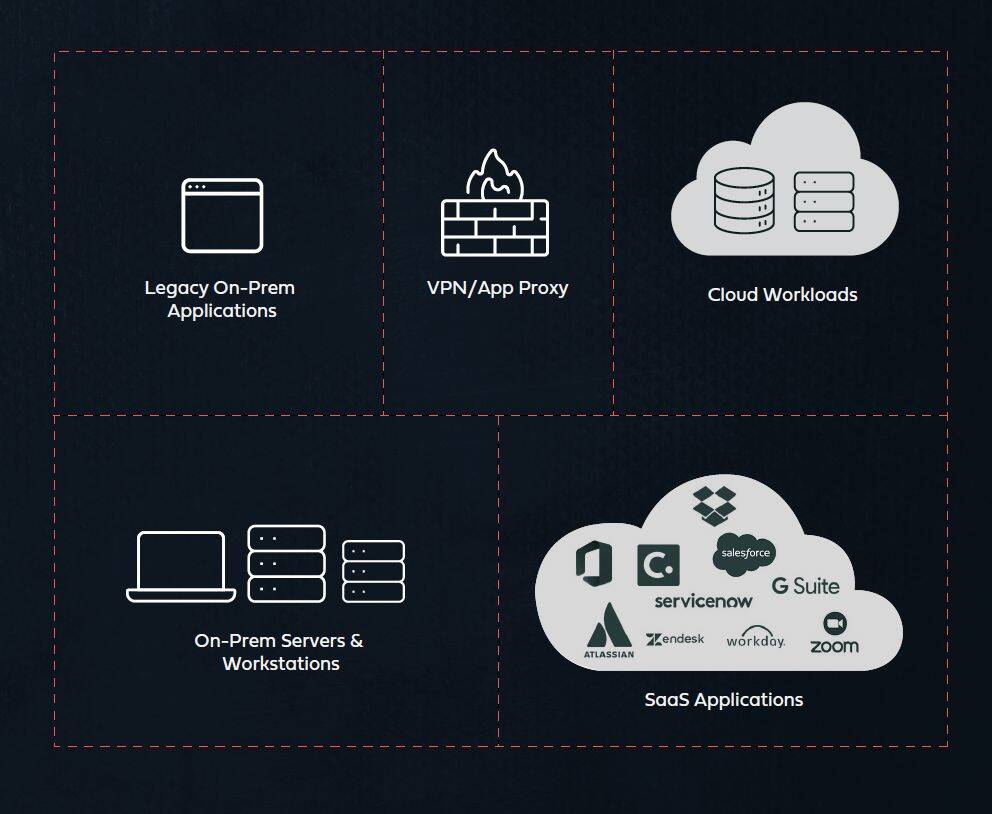
Multiple types of network, on-prem and cloud resources, each requiring a dedicated MFA solution.
Today’s IT environment is extremely versatile: VPN remote access, SaaS applications, RDP to on-prem machines, cloud workloads, and much more. Each of these often requires a different MFA solution (if more than one cloud IAM is used so there would also be a different MFA for each). The derived use of multiple MFA solutions entails operational complexities that directly degrades both:
User experience
Navigating through various products with different user interface is bound to create pushbacks from users and reduced coverage.
Level of protection
Using several different products, each with different risk calculation logic makes it difficult to maintain consistent protection level across all access policies.
MFA Challenge #3: Fragmentation

Re-evaluate your MFA: Are You as Protected as You Should Be?

85%
Nullam placerat, nulla ac ultricies euismod, mauris lacus gravida leo, id convallis justo massa eu urna.
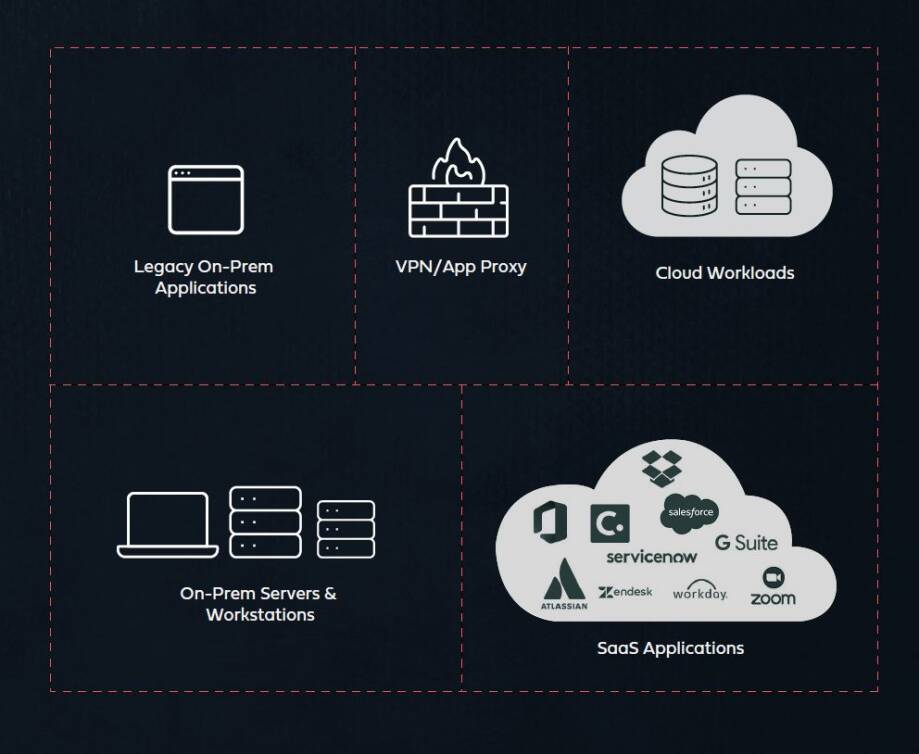
Multiple types of network, on-prem and cloud resources, each requiring a dedicated MFA solution.
Today’s IT environment is extremely versatile: VPN remote access, SaaS applications, RDP to on-prem machines, cloud workloads, and much more. Each of these often requires a different MFA solution (if more than one cloud IAM is used so there would also be a different MFA for each). The derived use of multiple MFA solutions entails operational complexities that directly degrades both:
User experience
Navigating through various products with different user interface is bound to create pushbacks from users and reduced coverage.
Level of protection
Using several different products, each with different risk calculation logic makes it difficult to maintain consistent protection level across all access policies.
MFA Challenge #3: Fragmentation