
Re-evaluate your MFA: Are You as Protected as You Should Be?

Common access interfaces to critical resources don’t support
standard MFA leaving them exposed to malicious access via compromised credentials
What are access interfaces?
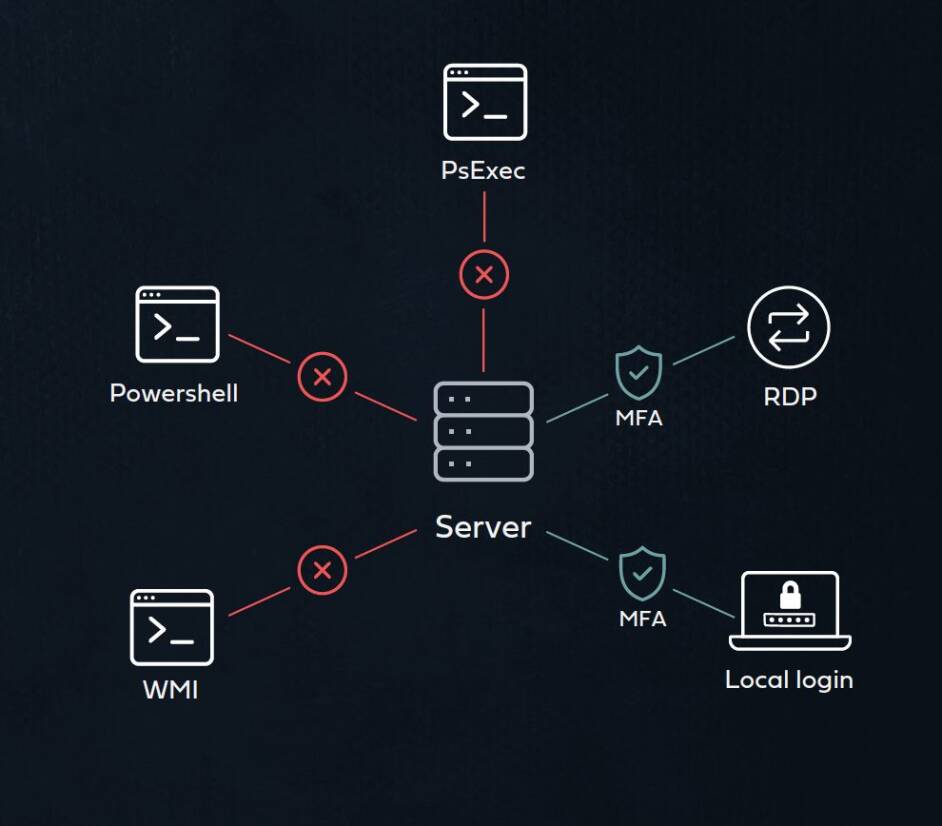
Access interfaces are various alternatives users can use to access a resource. Different resources vary in the type and number of access interface that they support. For a SaaS application, the main access interface would be browser log in. On the other hand, in the cased of a server (either physical or virtual) many access interfaces are used – RDP, SSH, local login and others.
Why does it matter?
Current MFA solutions are not consistent in their access interfaces’ coverage. While some access interfaces support MFA protection, others do not - including frequently used command line access tools such as CMD, remote PowerShell, WMI and others. Attackers intensively utilize these interfaces in lateral movement and ransomware attacks, and the inability to protect them with MFA creates a severe security weakness.
MFA Challenge #2:
Coverage Blind Spots

Re-evaluate your MFA: Are You as Protected as You Should Be?

85%
Nullam placerat, nulla ac ultricies euismod, mauris lacus gravida leo, id convallis justo massa eu urna.
Common access interfaces to critical resources don’t support
standard MFA leaving them exposed to malicious access via compromised credentials
What are access interfaces?
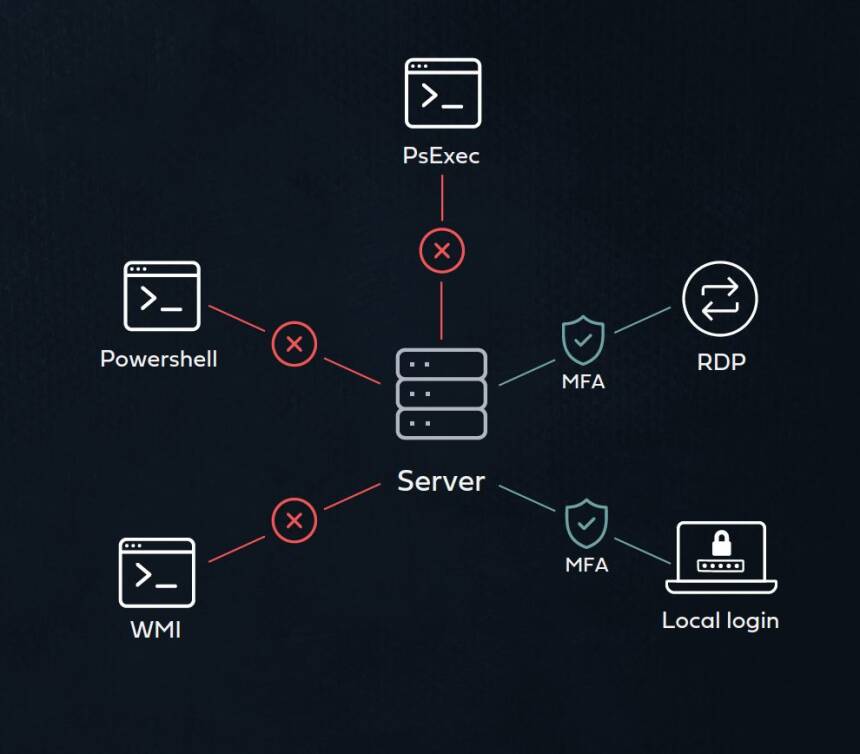
Access interfaces are various alternatives users can use to access a resource. Different resources vary in the type and number of access interface that they support. For a SaaS application, the main access interface would be browser log in. On the other hand, in the cased of a server (either physical or virtual) many access interfaces are used – RDP, SSH, local login and others.
Why does it matter?
Current MFA solutions are not consistent in their access interfaces’ coverage. While some access interfaces support MFA protection, others do not - including frequently used command line access tools such as CMD, remote PowerShell, WMI and others. Attackers intensively utilize these interfaces in lateral movement and ransomware attacks, and the inability to protect them with MFA creates a severe security weakness.
MFA Challenge #2:
Coverage Blind Spots