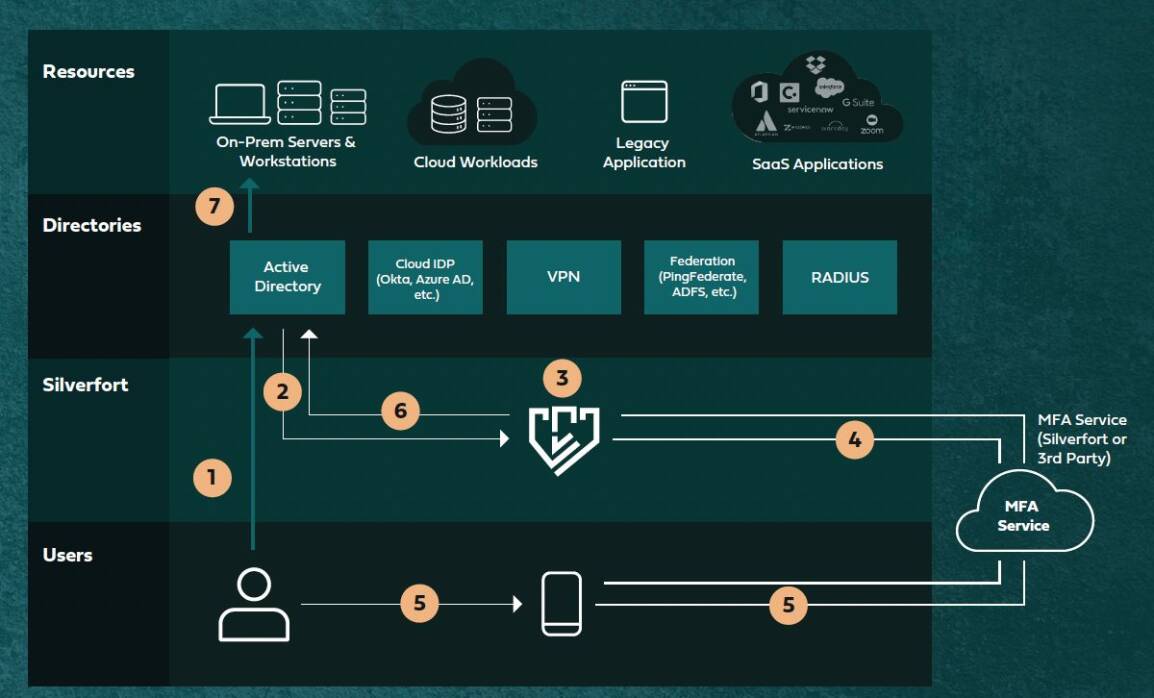
*A similar flow would apply upon attempting to access any other resource – the only change is the respective directory.

Re-evaluate your MFA: Are You as Protected as You Should Be?

Step-by-step walkthrough of Silverfort MFA for accessing on-prem server with remote Powershell in an Active Directory environment.
The user attempts to log in to a server with Powershell Enter-PSSessioncommand.
Active Directory forwards the request to Silverfort. Silverfort analyzes the risk of the access request.
Based on access policy, Silverfort utilizes either its own or a 3rd party MFA service to verify the user’s identity.
The user accepts the challenge and approves his/her identity.
Silverfort informs Active Directory that the user can be trusted to access theserver.
Active Directory returns the response to the unaware client/server and grants the user access.
Active Directory returns the response to the unaware client/server and grants the user access.
How Does That Work in Practice? Verification Flow Example Zoom-In

Re-evaluate your MFA: Are You as Protected as You Should Be?

85%
Nullam placerat, nulla ac ultricies euismod, mauris lacus gravida leo, id convallis justo massa eu urna.
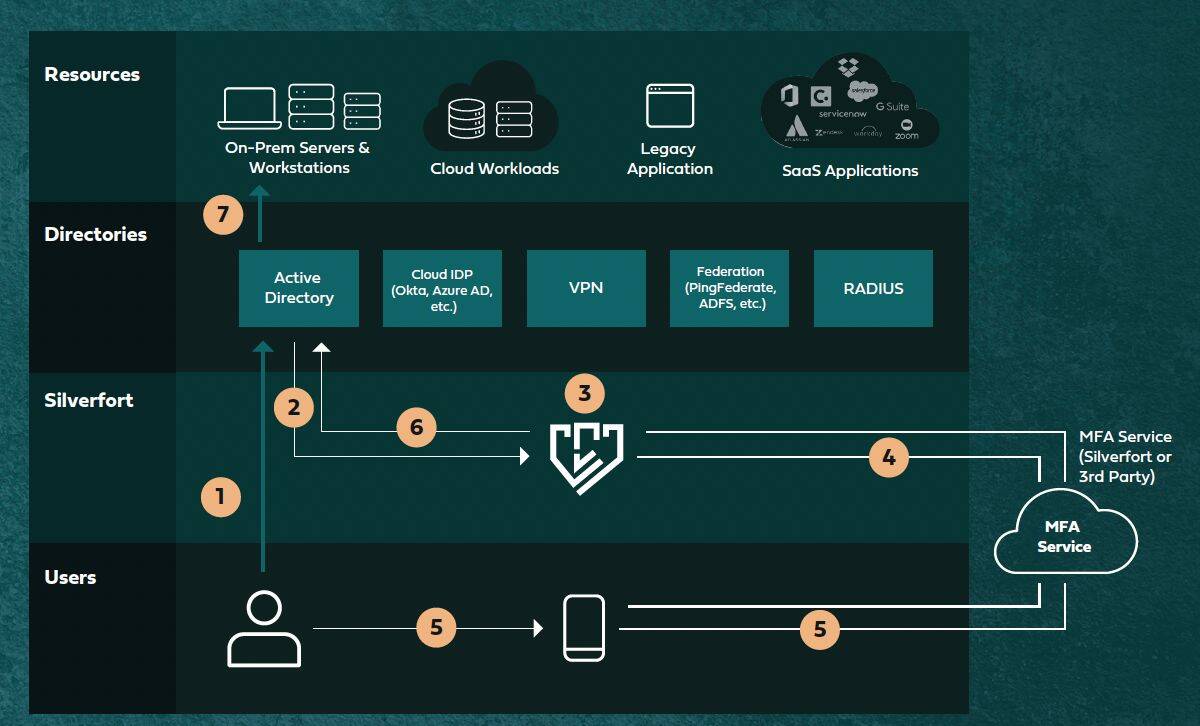
Step-by-step walkthrough of Silverfort MFA for accessing on-prem server with remote Powershell in an Active Directory environment.
The user attempts to log in to a server with Powershell Enter-PSSessioncommand.
Active Directory forwards the request to Silverfort. Silverfort analyzes the risk of the access request.
Based on access policy, Silverfort utilizes either its own or a 3rd party MFA service to verify the user’s identity.
The user accepts the challenge and approves his/her identity.
Silverfort informs Active Directory that the user can be trusted to access theserver.
Active Directory returns the response to the unaware client/server and grants the user access.
Active Directory returns the response to the unaware client/server and grants the user access.
How Does That Work in Practice? Verification Flow Example Zoom-In