
The Dark Side of Ransomware Protection Can you block lateral movement?

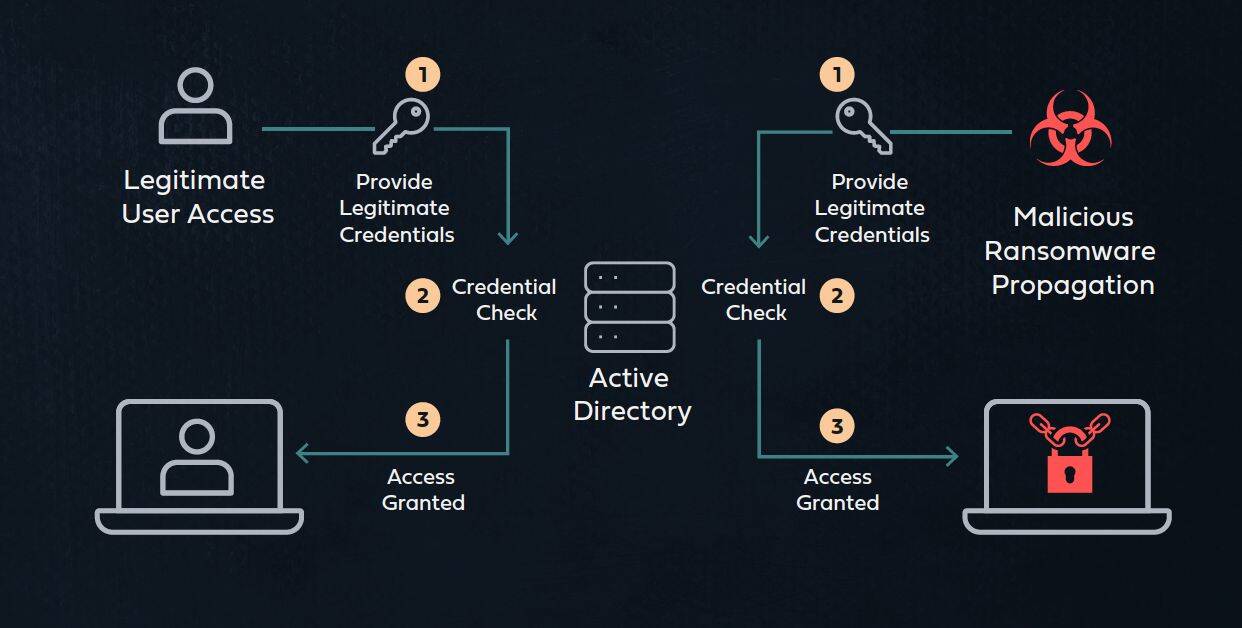
In an enterprise environment, connecting from one machine to another involves the first machine providing Active Directory with a username and password. If these match, Active Directory approves the connection. Ransomware propagation is carried out by connecting to multiple machines with compromised admin credentials.
Since these credentials are valid, Active Directory treats it as a legitimate authentication and grants the ransomware access.
What makes lateral movement a blind spot?

The Dark Side of Ransomware Protection Can you block lateral movement?

85%
Nullam placerat, nulla ac ultricies euismod, mauris lacus gravida leo, id convallis justo massa eu urna.
In an enterprise environment, connecting from one machine to another involves the first machine providing Active Directory with a username and password. If these match, Active Directory approves the connection. Ransomware propagation is carried out by connecting to multiple machines with compromised admin credentials.
Since these credentials are valid, Active Directory treats it as a legitimate authentication and grants the ransomware access.
What makes lateral movement a blind spot?