
The Dark Side of Ransomware Protection Can you block lateral movement?

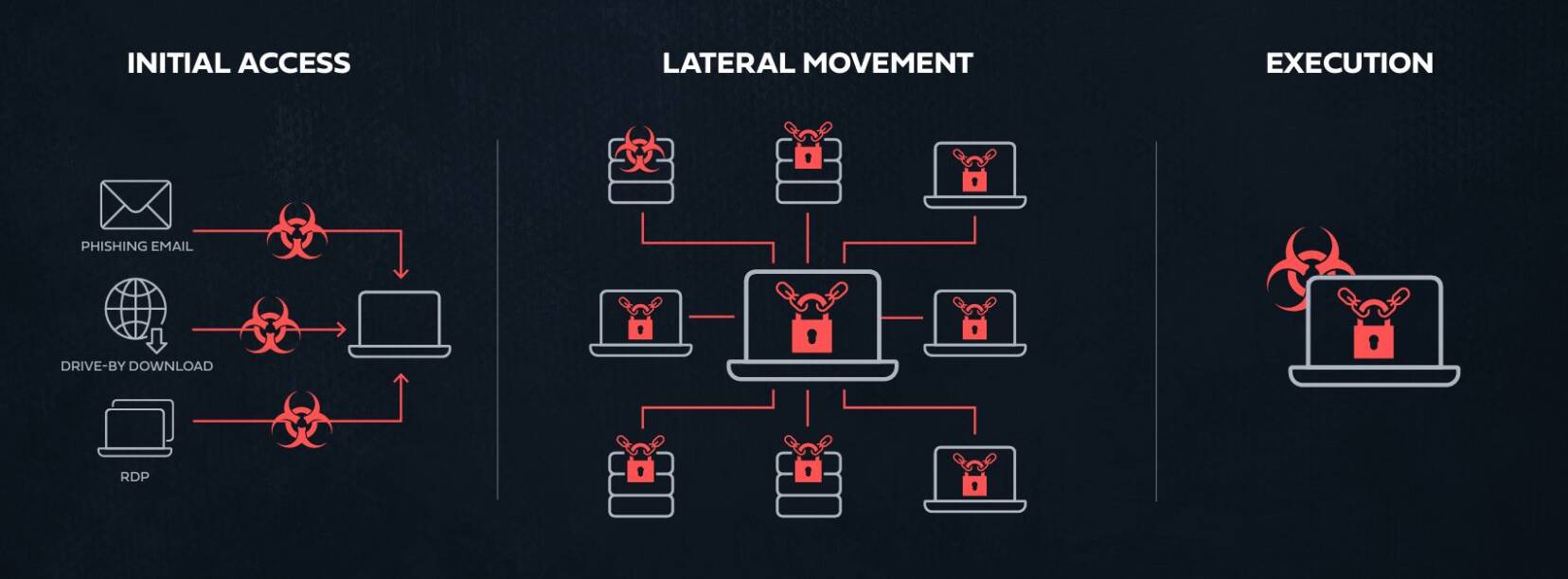
Ransomware attacks can be divided into three stages: Initial Access where the adversary gets an initial foothold in the environment, Lateral Movement where he\she expands it control to additional workstations and servers planting on them the ransomware payload, and finally the Execution of these payloads to encrypt or delete data files on the infected machines
The anatomy of ransomware attacks

The Dark Side of Ransomware Protection Can you block lateral movement?

85%
Nullam placerat, nulla ac ultricies euismod, mauris lacus gravida leo, id convallis justo massa eu urna.
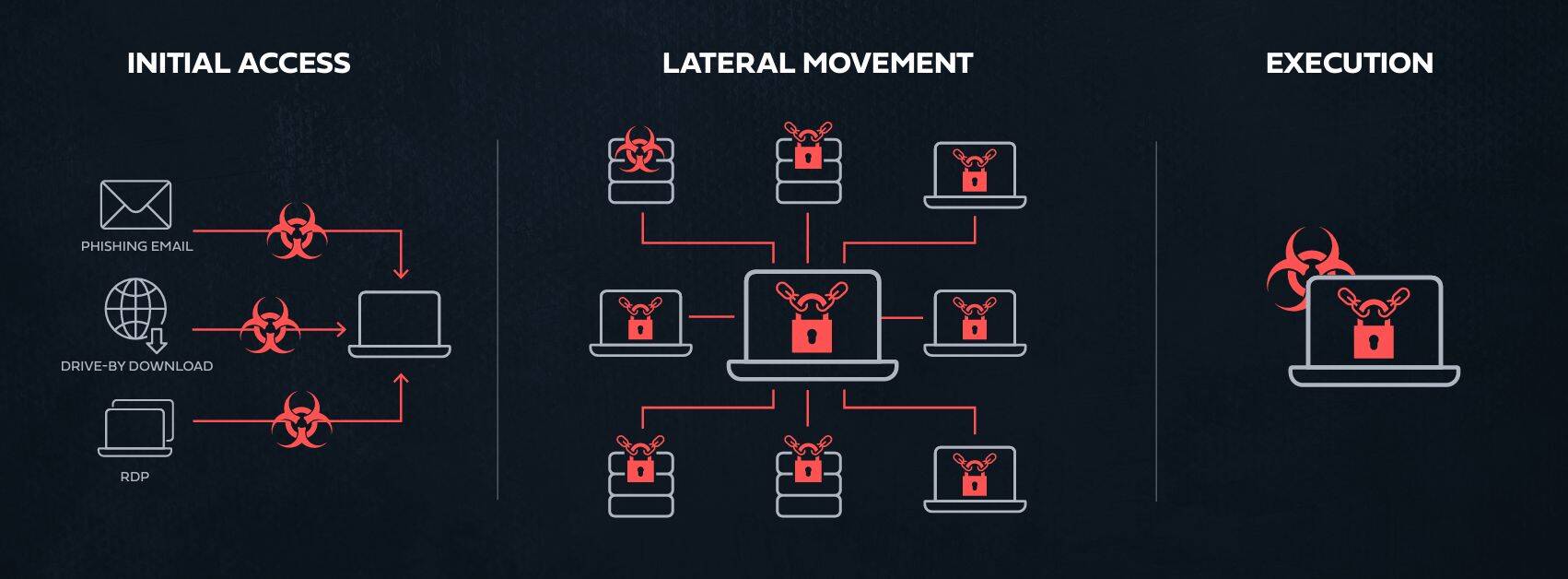
Ransomware attacks can be divided into three stages: Initial Access where the adversary gets an initial foothold in the environment, Lateral Movement where he\she expands it control to additional workstations and servers planting on them the ransomware payload, and finally the Execution of these payloads to encrypt or delete data files on the infected machines
The anatomy of ransomware attacks