
WHITEPAPER

CISO of a Fortune 100 Company
“Silverfort immediately helped us to mitigate the impact of compromised users. It was one of the most significant tools we used to analyze authentication flow/protocols and determine compromised identities as we brought our Domain Controllers back online. We worked quickly with the IR team to put blocking policies in place over the compromised identities.”
Using both MFA and block access policies prevents any malicious attempt to log in to additional resources. MFA is especially effective since it provides a clear indication of which accounts have been compromised, achieving both containment and discovery simultaneously. This will allow you to rapidly shut down an attack by automatically denying users access to resources until the attack has been eradicated and is in recovery mode. As soon as the attack has been fully contained by the policies in place, you can begin investigating further for the root cause and scope of the attack.
Following this, Silverfort offers access policies that block the service account (either a single account or a group) from accessing any resource outside of its normal behavior.
Block access policies for service accounts
Silverfort provides automated discovery of all service accounts.
IR teams can easily narrow down all service accounts that are potentially compromised by filtering using these risk indicators.
About Silverfort
Silverfort secures every dimension of identity. We are the first to deliver end-to-end identity security across the entire IAM infrastructure, eliminating gaps and blind spots, giving businesses visibility into their identity fabric and extending protection to resources that previously could not be protected. This is all done via a patented technology that natively integrates with your entire IAM infrastructure, Runtime Access Protection™ (RAP). It is lightweight, easy to use and deploy, and won’t disrupt business operations, resulting in better security outcomes with less work. Discover every identity across every environment, analyze exposures to reduce your attack surface, and enforce security controls inline to stop lateral movement, ransomware propagation, and other identity threats.
To learn more, visit www.silverfort.com
The entire IR lifecycle presents an opportunity to learn and improve. As every new threat demonstrates, there is a constant need to learn about new attacker techniques and keep up with the latest attack methods, technologies, strategies, and procedures. Attackers are constantly evolving, and so should an incident response team.
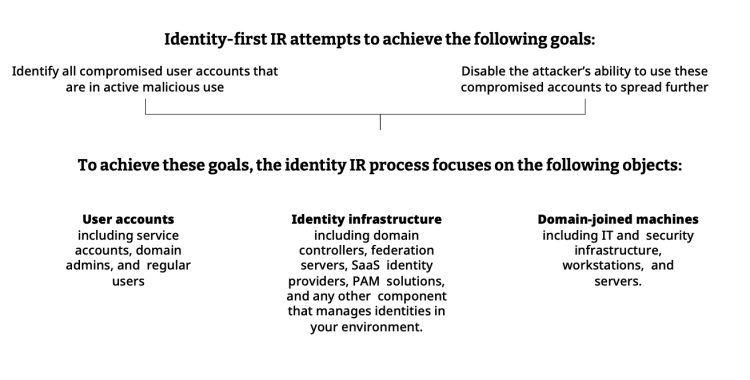
As identity threats continue to increase in number and sophistication, attackers will treat compromising users’ credentials as a key tool in their toolbox. IR teams must have the tools necessary to conduct an effective and efficient identity IR process to identify and contain compromised identities and eliminate attackers.
Using this screen, Silverfort empowers IR teams with continuous visibility and actionable insights into everything identity-related. Now IR teams can implement a more proactive approach to their identity security posture management within their environment.
Having such a system in place will enable your organization to be well prepared to deal with the compromise of identity infrastructure, as well as detect and block malicious access to compromised accounts in the future.
During this stage, Silverfort enables IR teams to proactively prepare their environment to mitigate any incoming identity threats. Silverfort provides IR teams with an Insights screen that aggregates all identity security weaknesses and exposures such as shadow admins, NTLMv1, and many other identity protection gaps that threat actors typically abuse.
The post-incident stage begins once the typical IR procedures have eliminated the threat. In this stage, the incident response team restores normal operations to the systems and users. Compromised accounts are secured and should have more secure access controls; you will begin to reinstate access securely, enforcing MFA for all privileged access and monitoring for attempts to use compromised users, even if they are already disabled.
With Silverfort, the detection of compromised users will often be the first validated finding in the IR process. In such cases, it can also expedite and optimize the rest of the process.
For example, the compromised users’ source and destination machines are immediate candidates for quarantine and searching for malicious artifacts (unique files, disk manipulation, outbound network connections, etc.). Taking this route is much more efficient than blindly applying these investigation procedures to all machines in the environment.
This can be done by reviewing the user’s authentication history. Once these machines have been identified, standard Incident Response (IR) procedures can be applied to these machines to detect any malware or malicious outbound traffic.
Once Silverfort has validated that a user has been compromised, the next step is to disable or reset the user’s password. This is crucial in preventing further unauthorized access to the system using compromised credentials.
Kerberoasting: The Kerberoasting technique targets privileged service accounts with an associated Security Principal Name (SPN), enabling attackers to decrypt their hash offline and get their password.
Service accounts are highly targeted by threat actors.
Silverfort provides unique risk indicators to assist IR teams in detecting a compromise:
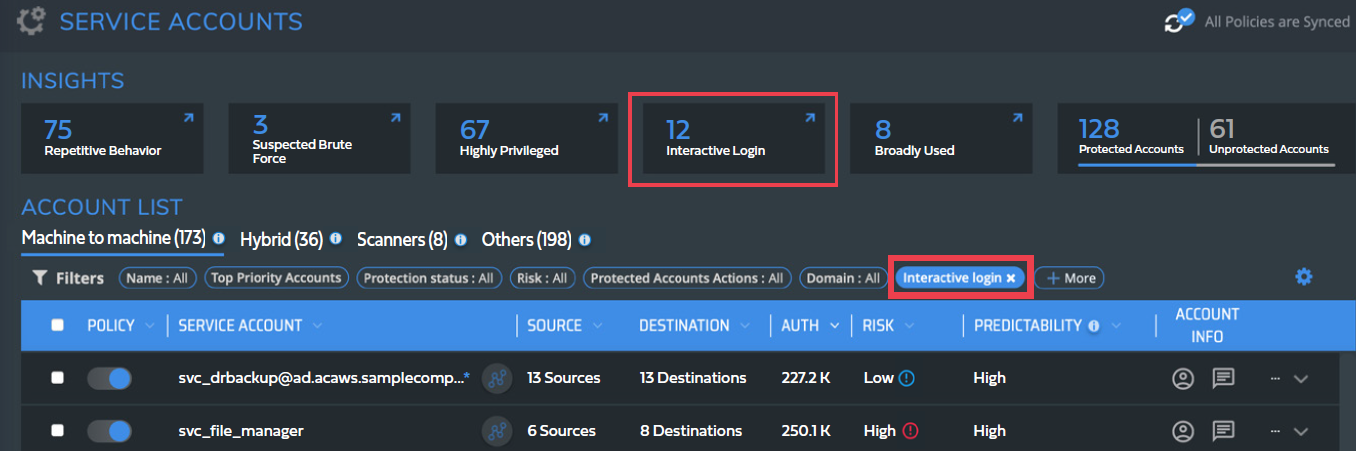
Service account interactive login: Service accounts are used for machine-to-machine communication, so an interactive login with a service account is a suspicious event that could indicate compromise and abuse.
Manual detection via log screen:
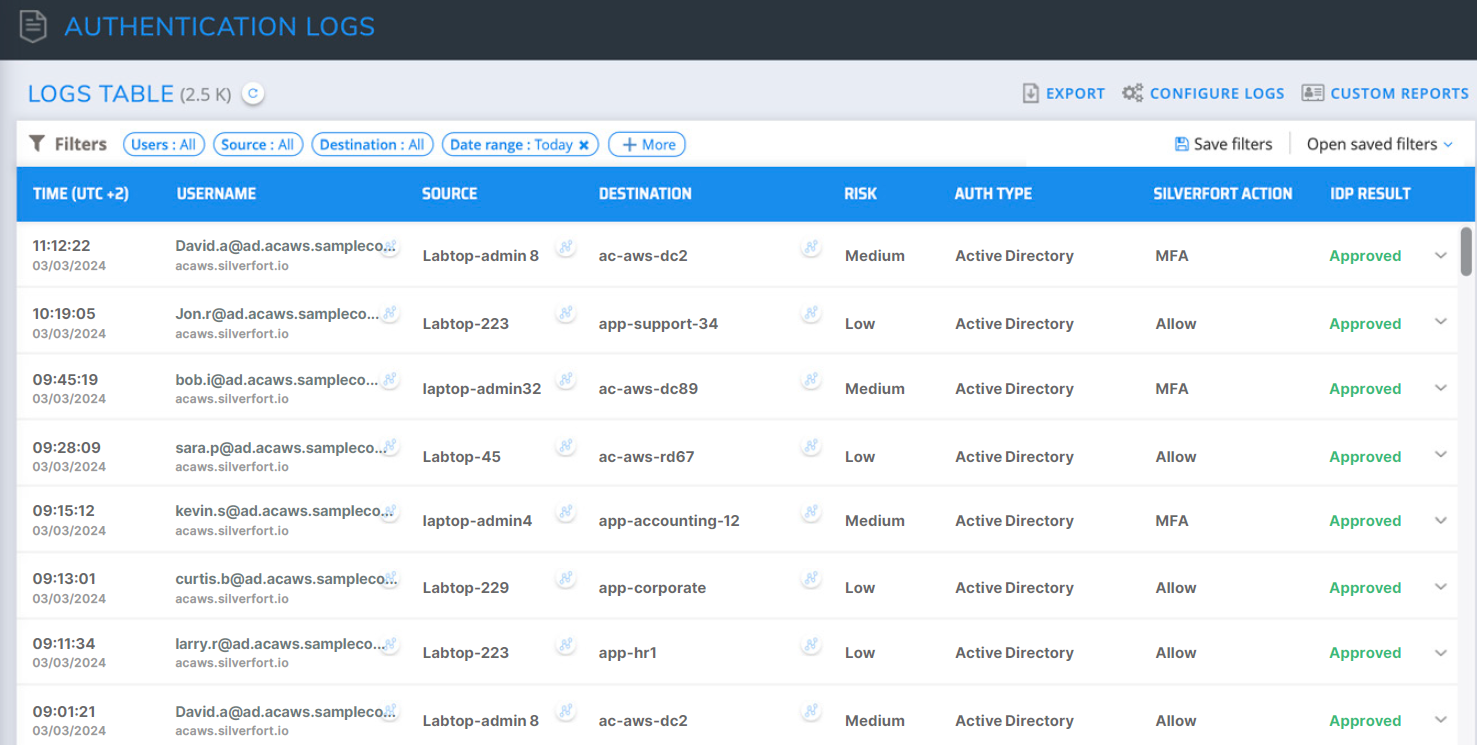
For this stage, Silverfort provides IR teams with a detailed Log Screen that includes an aggregated view of authentications and access attempts made by all users and service accounts to any cloud or on-prem resource. Every authentication is assigned a risk score by Silverfort’s risk engine, along with a wide range of filters to easily detect and investigate authentications initiated by malicious actors, such as:
Excessive and anomalous activity
Interactive login by a service account
Newly created/enabled accounts
Automated activity
Malicious IP addresses and bad geolocation
IT teams get all the data they need to spot the users who perform anomalous behavior that potentially indicates a compromise.
Silverfort threat detection capabilities detect and analyze abnormal authentication patterns that could indicate additional compromised users.
Silverfort provides two ways to detect compromised user accounts
Automated detection via policy violations:
IR teams will be automatically alerted by Silverfort when a compromised user account is still being used by a malicious actor. This occurs when a user is part of a group that has been assigned a deny or MFA policy. This enables IR teams to quickly spot the compromised users and mitigate the threats. Filtering all users with ‘MFA blocked’ on the Log Screen provides this in a single click.
Block access policies for users and admins will prevent access altogether
This is useful in emergency cases where containment is more important than operational continuity. As a result, it allows the isolation of a single compromised user or service account, similar to the isolation of endpoints in an EDR. It’s less about enforcing an all-around blockade and more about elevating protection around specific critical resources such as the DC or other infrastructure components.
Traditionally, detection of malicious activity is a prerequisite for applying any containment actions. However, Silverfort enables you to change that and start the IR process with a complete malicious access lockdown.
Depending on the intensity and scope of the ongoing attack, you can control the level of this lockdown and determine the balance between MFA and block access policies. In most cases, MFA would achieve the same containment results as block access, while allowing legitimate users to continue accessing resources. To achieve this, Silverfort provides the following capabilities:
MFA policies for users and admins
Configure MFA and block access policies for any user account or user group. A single policy can apply to all users and resources if necessary. Once the policy is activated, any additional attempt from the attacker’s side to use the compromised accounts for malicious access would challenge the true user with MFA, blocking the attacker’s access upon denial. This applies to any authentication type, including command-line access over PsExec, PowerShell, or WMI, which are typically used by adversaries.
Silverfort is the first solution that provides IR teams with identity incident response capabilities in a single, easily deployed solution. Silverfort’s Identity IR playbook is mapped to the NIST IR framework’s recommended steps, but we believe the order of these steps needs to be rearranged to be most effective.
The NIST framework divides the IR process into best practices across the following stages:
Preparation
Detection and analysis
Containment, eradication and recovery
Post-incident activity
The most relevant to identity IR is stage 2 (detection and analysis) and stage 3 (containment, eradication and recovery).
NIST emphasizes that IR is not a linear process but a cyclical one, especially between the second and third stages.
This principle is well illustrated when using Silverfort in the IR process. As you’ll soon see, Silverfort’s unique capabilities in MFA and block access in AD environments enable it to perform these stages simultaneously. Let’s see how this is done.
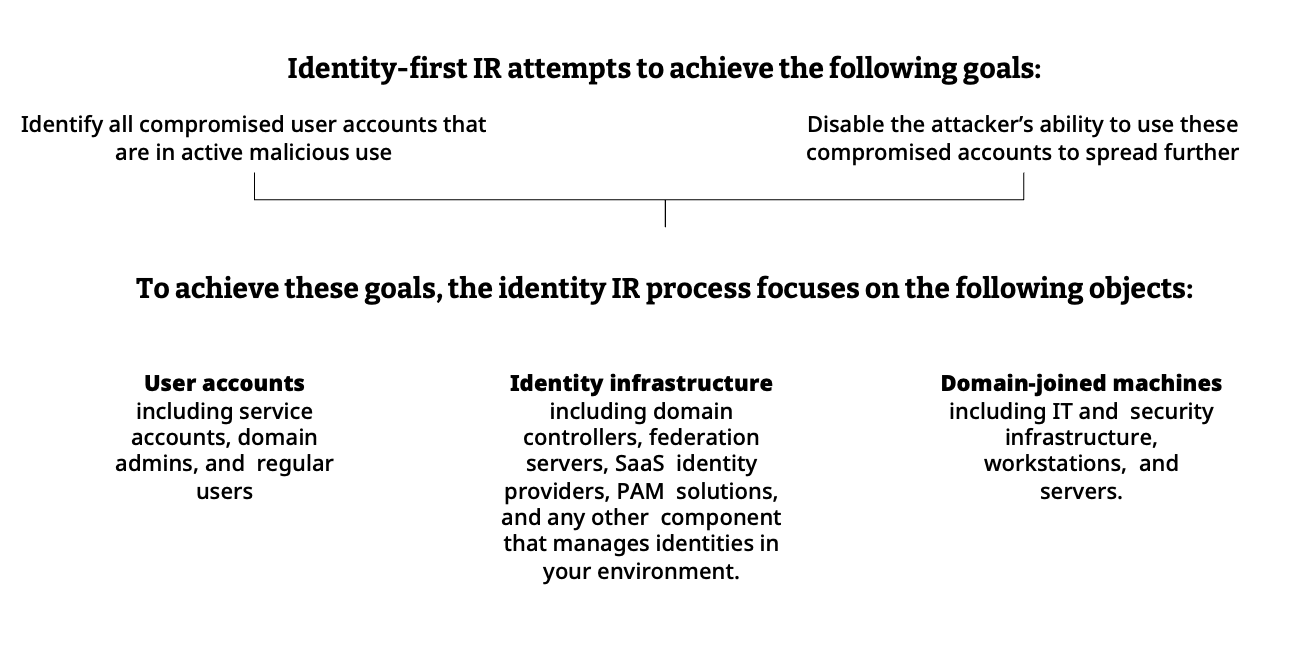
Note that these goals can be achieved using EDR, SIEM, or the standard IR toolkit. However, taking this route entails a long, manual, and error-prone process that takes place while the attack is still in full flow. The purpose of identity IR is to achieve them in a rapid, efficient, and nearly fully automated manner while gaining authentication and user visibility in real time.
Once these goals are achieved, the identity IR merges into the overall IR process to eradicate all malicious presence from the targeted environment.
An organization’s Incident Response Plan (IRP) is the set of processes followed by security teams to respond to an attack. It usually includes detecting the attack’s scope, containing it to prevent further spread, and eradicating adversarial presence and activities.
While there’s an established IR playbook to handle the malware and network aspects of cyberattacks, the identity aspect is lacking. There are no common procedures to identify compromised user accounts and prevent attackers from using them to spread within the targeted environment rapidly and efficiently.
This whitepaper fills this gap by providing an identity IR playbook using Silverfort’s identity security platform. It encloses the aggregated experience of multiple customers who have used it to expedite and optimize their IR processes.
Identity IR refers to all identity-related TTPs, including credential access, privilege escalation, and lateral movement. It complements the existing IR practices that address parallel attack manifestations, such as malware and malicious network traffic, to enhance and accelerate the overall response process.
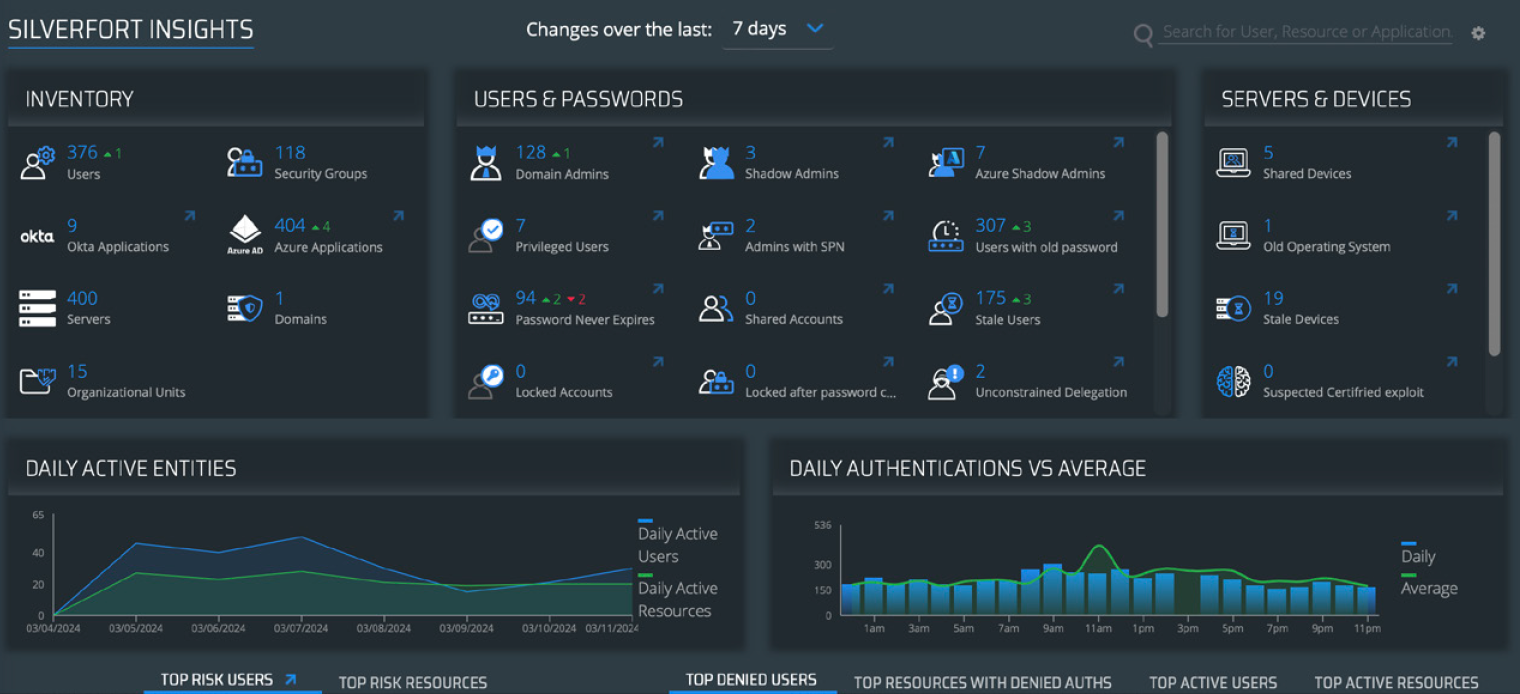
The Silverfort Insights screen offers insights into users, servers, applications, and devices protected by Silverfort
In the Recovery stage, Silverfort Logs screen highlights everything is back to normal
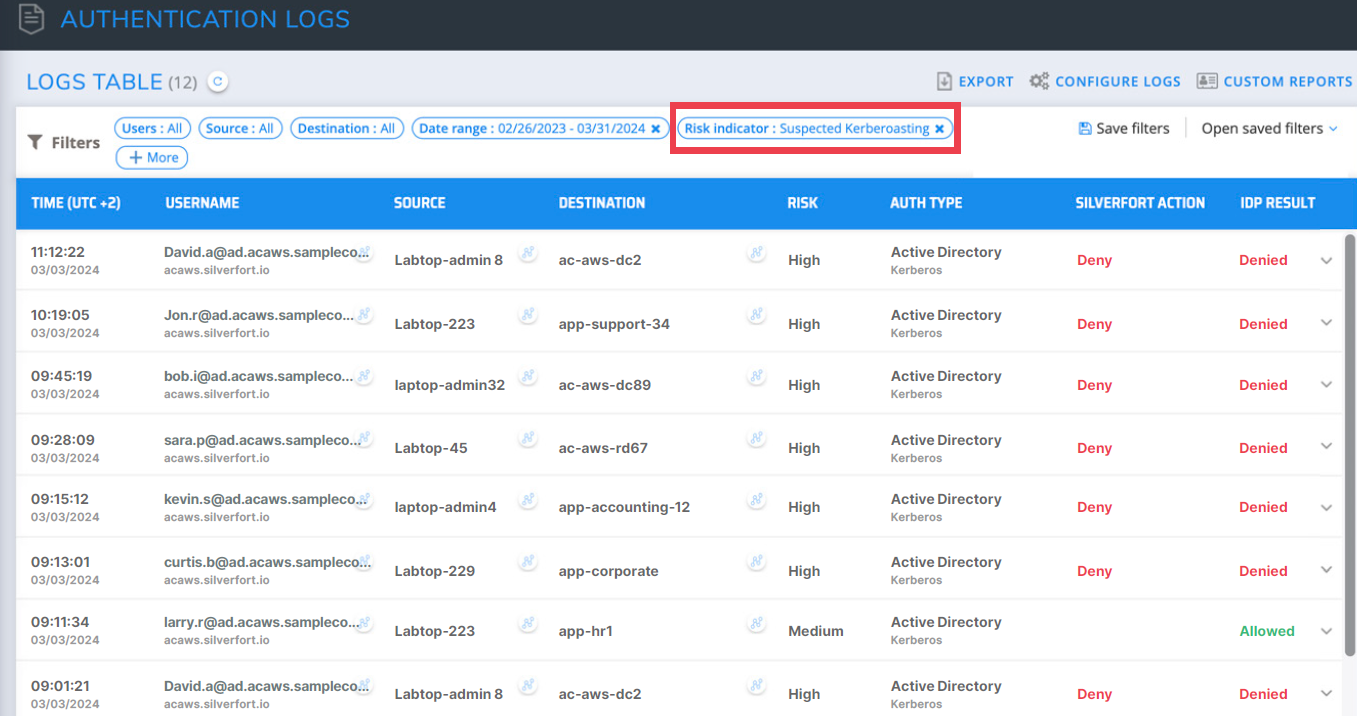
Filtering for service accounts suspected of Kerberoasting in the logs screen
Filtering for interactive login with service accounts in the Silverfort service accounts screen
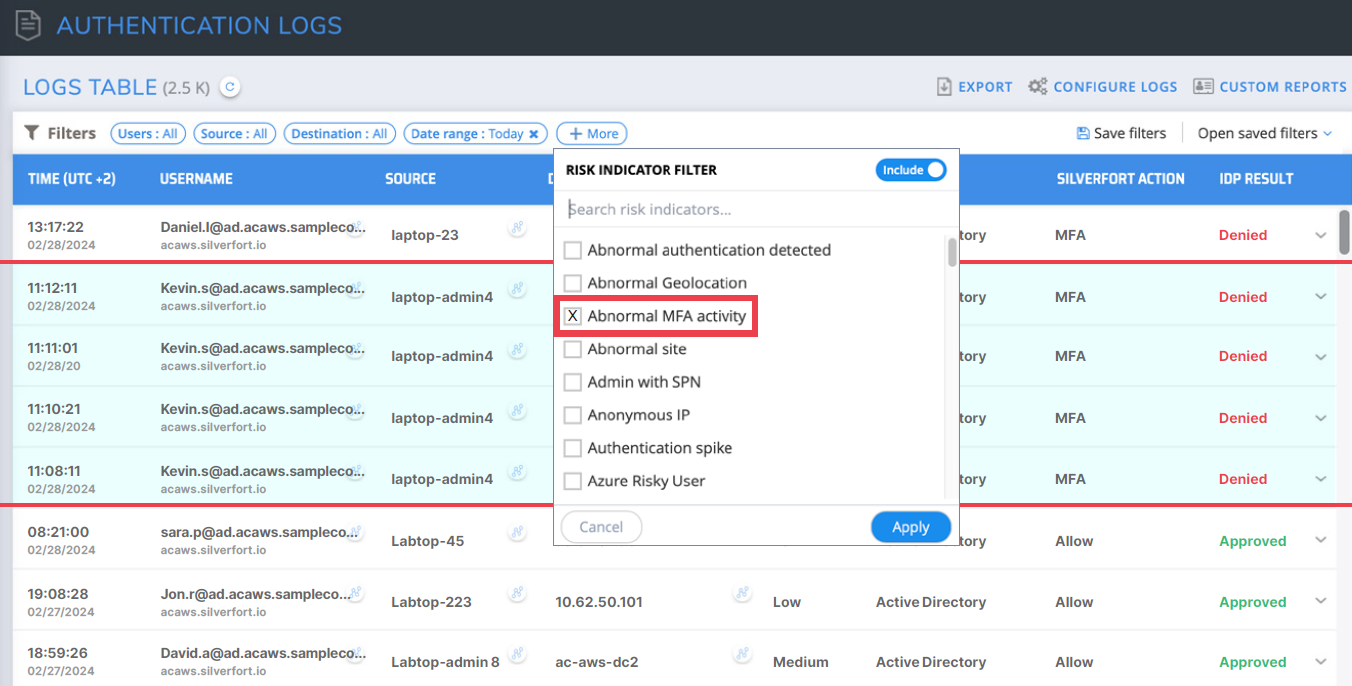
Filtering for abnormal MFA activity in the logs screen
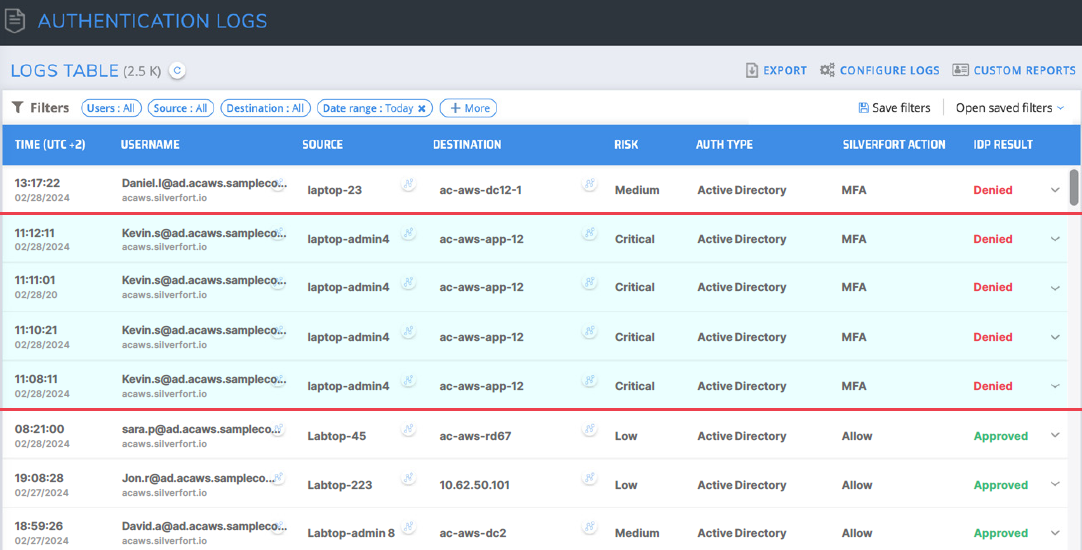
Silverfort automatically detects and alerts of compromised users in the Silverfort authentication log screen
Silverfort’s service account policy screen allows admins to choose sources, destinations, authentication protocols, when policies should be applied, and what actions the system should take
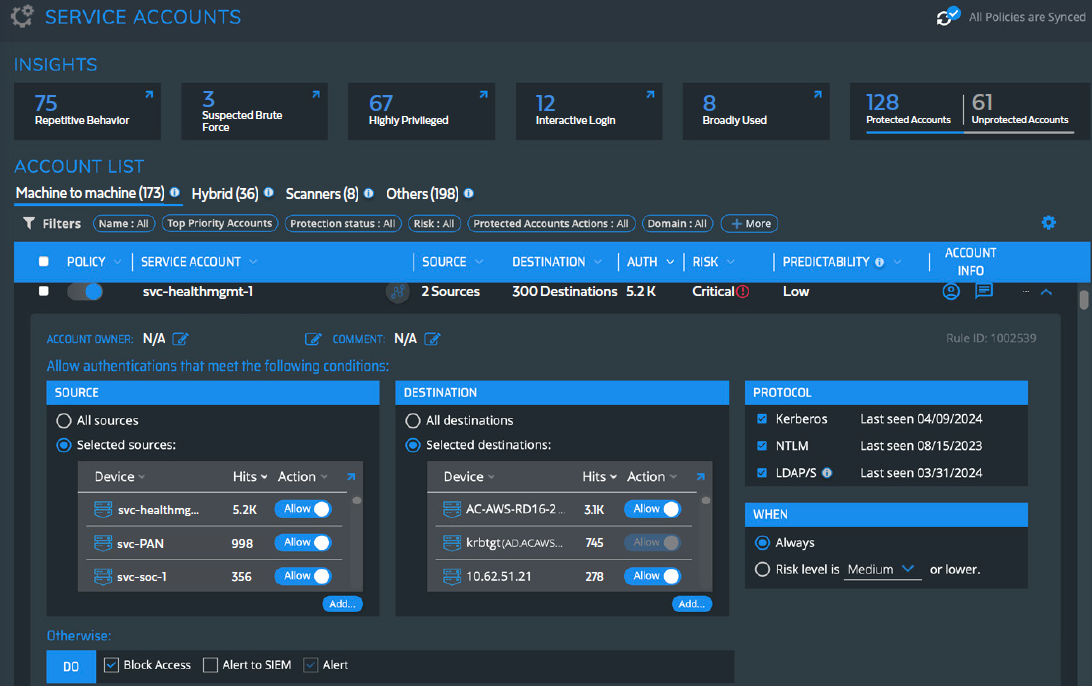
Silverfort’s service account policy screen allows admins to choose sources, destinations, authentication protocols, when policies should be applied, and what actions the system should take

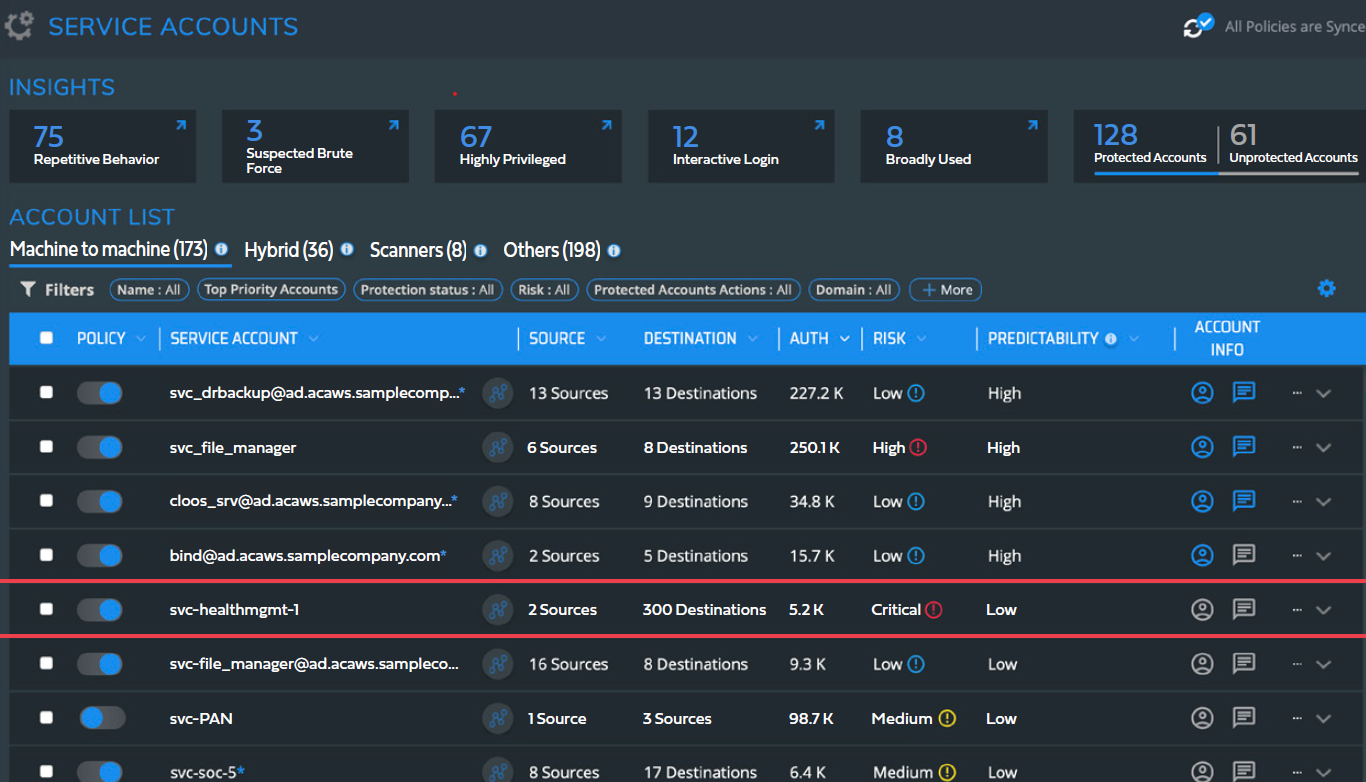
Silverfort’s Service Accounts screen displays the service account name, source, destination, number of authentications, risk score, and account info
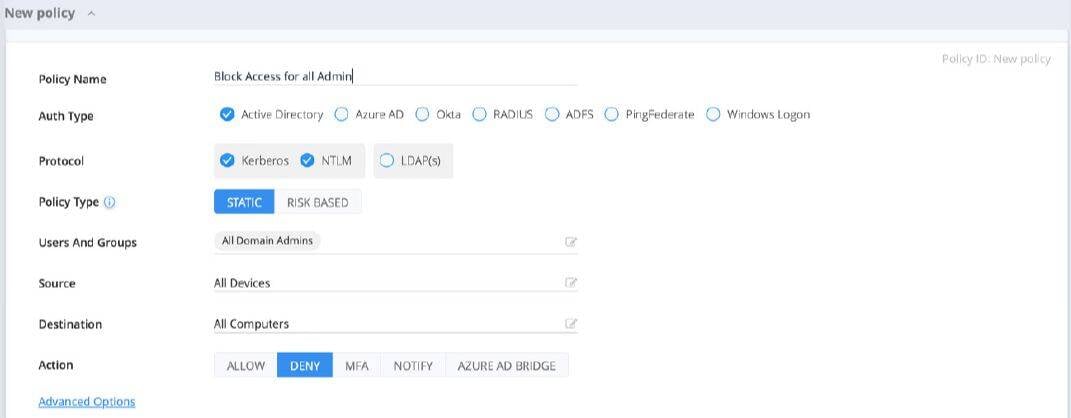
Silverfort policy blocks all access for all admins
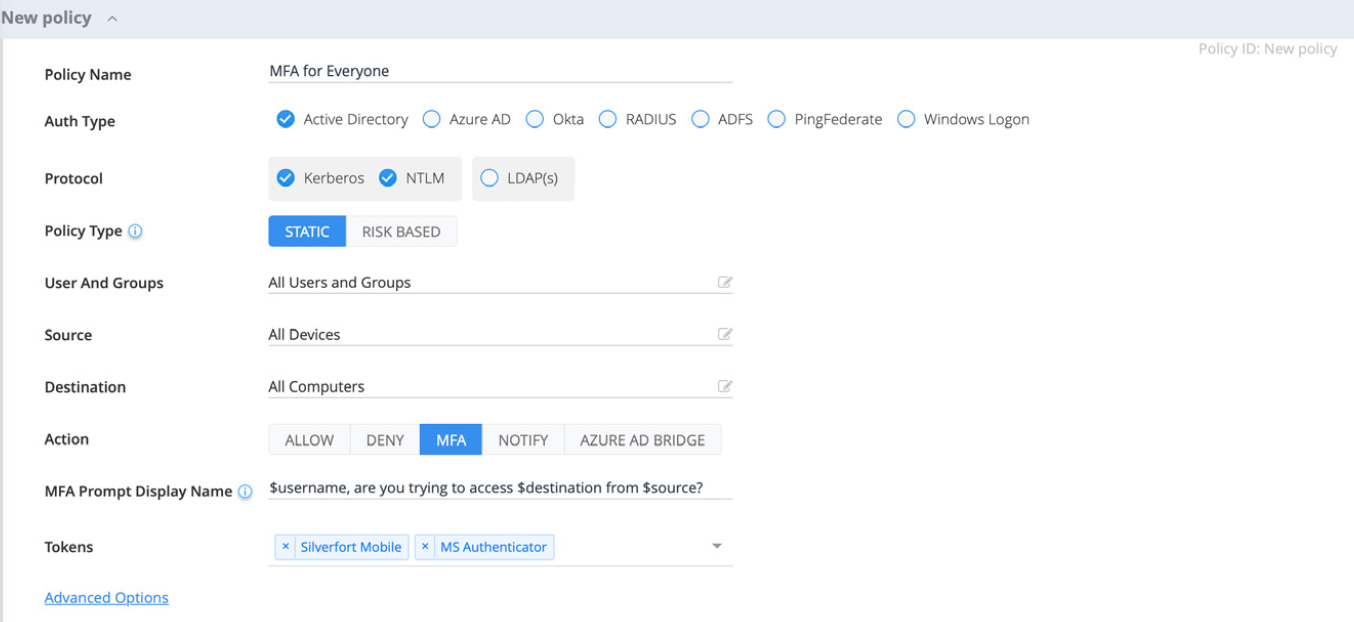
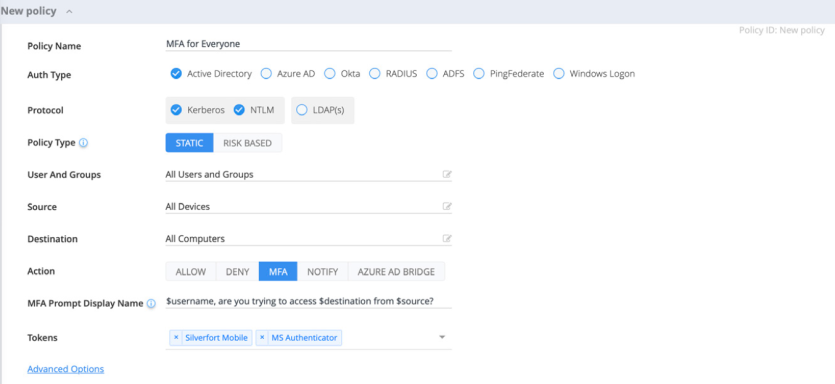
Silverfort policy enforces MFA to all accounts and resources



About Silverfort
Silverfort secures every dimension of identity. We are the first to deliver end-to-end identity security across the entire IAM infrastructure, eliminating gaps and blind spots, giving businesses visibility into their identity fabric and extending protection to resources that previously could not be protected. This is all done via a patented technology that natively integrates with your entire IAM infrastructure, Runtime Access Protection™ (RAP). It is lightweight, easy to use and deploy, and won’t disrupt business operations, resulting in better security outcomes with less work. Discover every identity across every environment, analyze exposures to reduce your attack surface, and enforce security controls inline to stop lateral movement, ransomware propagation, and other identity threats.
To learn more, visit www.silverfort.com
The entire IR lifecycle presents an opportunity to learn and improve. As every new threat demonstrates, there is a constant need to learn about new attacker techniques and keep up with the latest attack methods, technologies, strategies, and procedures. Attackers are constantly evolving, and so should an incident response team.
As identity threats continue to increase in number and sophistication, attackers will treat compromising users’ credentials as a key tool in their toolbox. IR teams must have the tools necessary to conduct an effective and efficient identity IR process to identify and contain compromised identities and eliminate attackers.
Using this screen, Silverfort empowers IR teams with continuous visibility and actionable insights into everything identity-related. Now IR teams can implement a more proactive approach to their identity security posture management within their environment.
The Silverfort Insights screen offers insights into users, servers, applications, and devices protected by Silverfort
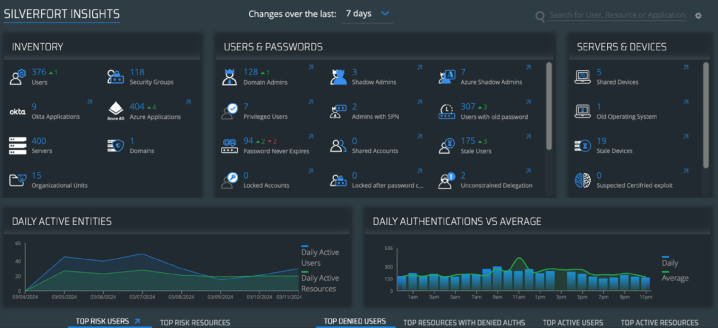
Having such a system in place will enable your organization to be well prepared to deal with the compromise of identity infrastructure, as well as detect and block malicious access to compromised accounts in the future.
During this stage, Silverfort enables IR teams to proactively prepare their environment to mitigate any incoming identity threats. Silverfort provides IR teams with an Insights screen that aggregates all identity security weaknesses and exposures such as shadow admins, NTLMv1, and many other identity protection gaps that threat actors typically abuse.
In the Recovery stage, Silverfort Logs screen highlights everything is back to normal
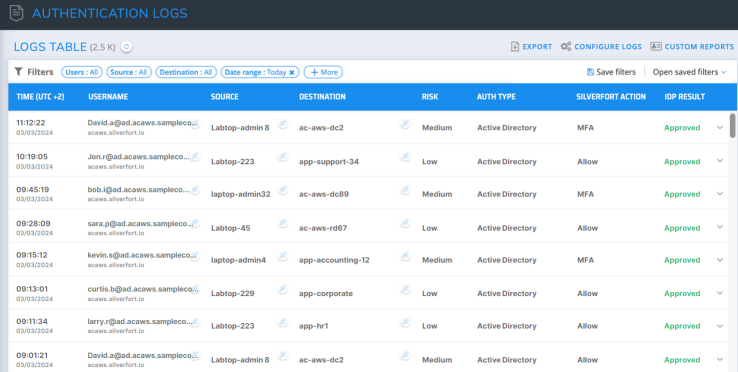
The post-incident stage begins once the typical IR procedures have eliminated the threat. In this stage, the incident response team restores normal operations to the systems and users. Compromised accounts are secured and should have more secure access controls; you will begin to reinstate access securely, enforcing MFA for all privileged access and monitoring for attempts to use compromised users, even if they are already disabled.
With Silverfort, the detection of compromised users will often be the first validated finding in the IR process. In such cases, it can also expedite and optimize the rest of the process.
For example, the compromised users’ source and destination machines are immediate candidates for quarantine and searching for malicious artifacts (unique files, disk manipulation, outbound network connections, etc.). Taking this route is much more efficient than blindly applying these investigation procedures to all machines in the environment.
This can be done by reviewing the user’s authentication history. Once these machines have been identified, standard Incident Response (IR) procedures can be applied to these machines to detect any malware or malicious outbound traffic.
Once Silverfort has validated that a user has been compromised, the next step is to disable or reset the user’s password. This is crucial in preventing further unauthorized access to the system using compromised credentials.
IR teams can easily narrow down all service accounts that are potentially compromised by filtering using these risk indicators.
Filtering for service accounts suspected of Kerberoasting in the logs screen
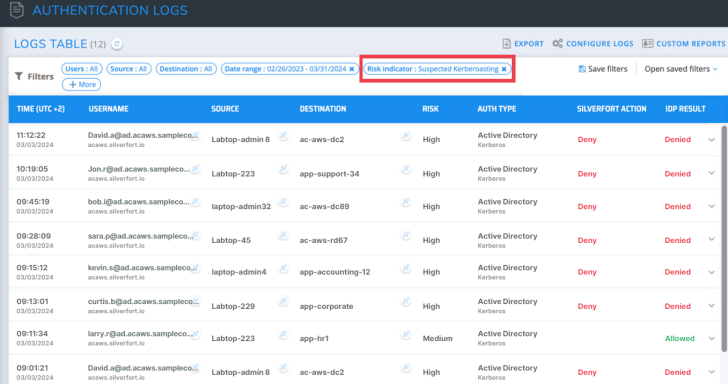
Kerberoasting: The Kerberoasting technique targets privileged service accounts with an associated Security Principal Name (SPN), enabling attackers to decrypt their hash offline and get their password.
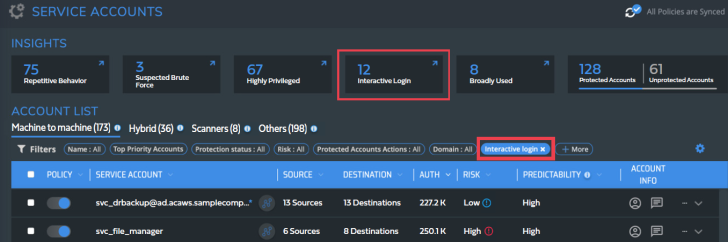
Filtering for interactive login with service accounts in the Silverfort service accounts screen
Service accounts are highly targeted by threat actors.
Silverfort provides unique risk indicators to assist IR teams in detecting a compromise:
Service account interactive login: Service accounts are used for machine-to-machine communication, so an interactive login with a service account is a suspicious event that could indicate compromise and abuse.
Service accounts are highly targeted by threat actors.
Silverfort provides unique risk indicators to assist IR teams in detecting a compromise:
Service account interactive login: Service accounts are used for machine-to-machine communication, so an interactive login with a service account is a suspicious event that could indicate compromise and abuse.
Filtering for abnormal MFA activity in the logs screen
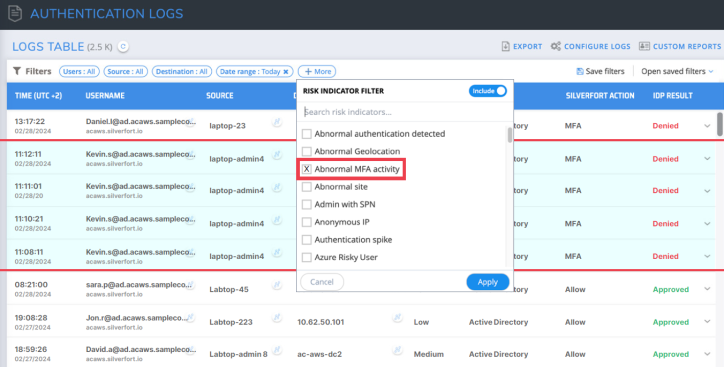
Manual detection via log screen:
For this stage, Silverfort provides IR teams with a detailed Log Screen that includes an aggregated view of authentications and access attempts made by all users and service accounts to any cloud or on-prem resource. Every authentication is assigned a risk score by Silverfort’s risk engine, along with a wide range of filters to easily detect and investigate authentications initiated by malicious actors, such as:
Excessive and anomalous activity
Interactive login by a service account
Newly created/enabled accounts
Automated activity
Malicious IP addresses and bad geolocation
IT teams get all the data they need to spot the users who perform anomalous behavior that potentially indicates a compromise.
Silverfort automatically detects and alerts of compromised users in the Silverfort authentication log screen
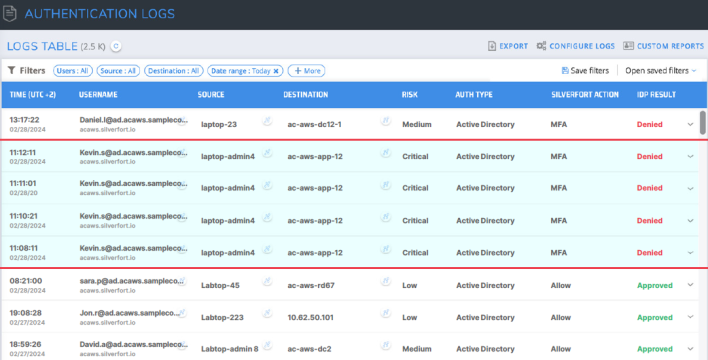
Silverfort threat detection capabilities detect and analyze abnormal authentication patterns that could indicate additional compromised users.
Silverfort provides two ways to detect compromised user accounts
Automated detection via policy violations:
IR teams will be automatically alerted by Silverfort when a compromised user account is still being used by a malicious actor. This occurs when a user is part of a group that has been assigned a deny or MFA policy. This enables IR teams to quickly spot the compromised users and mitigate the threats. Filtering all users with ‘MFA blocked’ on the Log Screen provides this in a single click.
Using both MFA and block access policies prevents any malicious attempt to log in to additional resources. MFA is especially effective since it provides a clear indication of which accounts have been compromised, achieving both containment and discovery simultaneously. This will allow you to rapidly shut down an attack by automatically denying users access to resources until the attack has been eradicated and is in recovery mode. As soon as the attack has been fully contained by the policies in place, you can begin investigating further for the root cause and scope of the attack.

Silverfort’s service account policy screen allows admins to choose sources, destinations, authentication protocols, when policies should be applied, and what actions the system should take
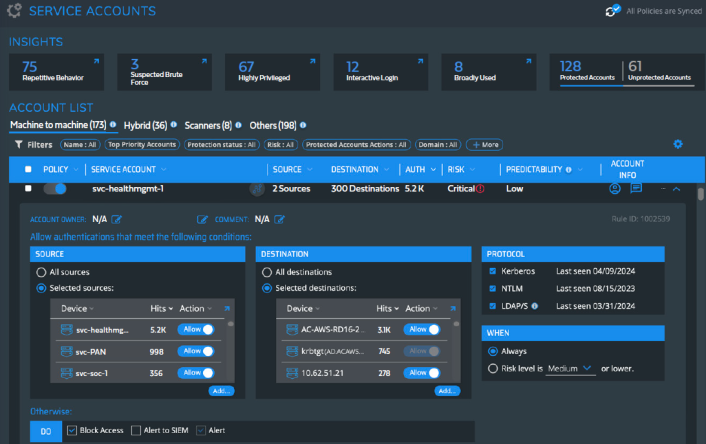
Following this, Silverfort offers access policies that block the service account (either a single account or a group) from accessing any resource outside of its normal behavior.
Silverfort’s Service Accounts screen displays the service account name, source, destination, number of authentications, risk score, and account info
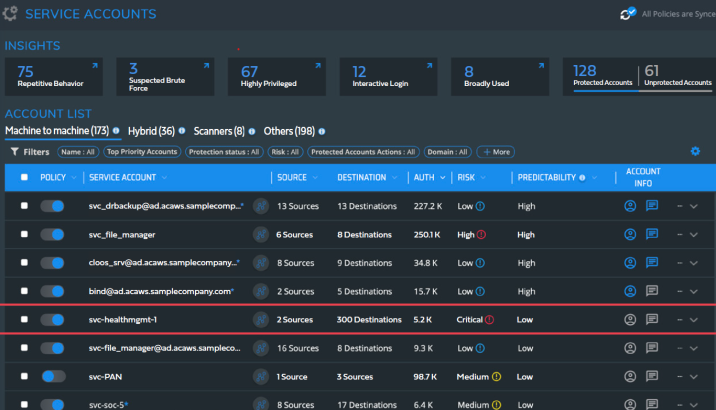
Block access policies for service accounts
Silverfort provides automated discovery of all service accounts.
Block access policies for users and admins will prevent access altogether
This is useful in emergency cases where containment is more important than operational continuity. As a result, it allows the isolation of a single compromised user or service account, similar to the isolation of endpoints in an EDR. It’s less about enforcing an all-around blockade and more about elevating protection around specific critical resources such as the DC or other infrastructure components.
Silverfort policy blocks all access for all admins
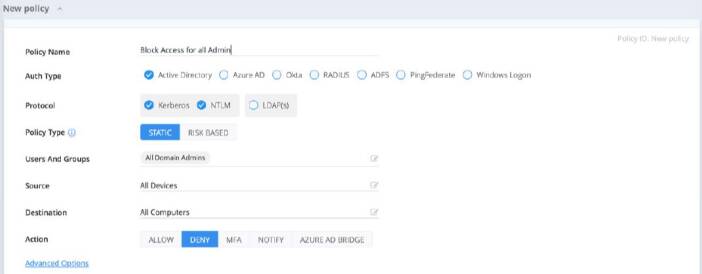
Traditionally, detection of malicious activity is a prerequisite for applying any containment actions. However, Silverfort enables you to change that and start the IR process with a complete malicious access lockdown.
Depending on the intensity and scope of the ongoing attack, you can control the level of this lockdown and determine the balance between MFA and block access policies. In most cases, MFA would achieve the same containment results as block access, while allowing legitimate users to continue accessing resources. To achieve this, Silverfort provides the following capabilities:
MFA policies for users and admins
Configure MFA and block access policies for any user account or user group. A single policy can apply to all users and resources if necessary. Once the policy is activated, any additional attempt from the attacker’s side to use the compromised accounts for malicious access would challenge the true user with MFA, blocking the attacker’s access upon denial. This applies to any authentication type, including command-line access over PsExec, PowerShell, or WMI, which are typically used by adversaries.
Silverfort is the first solution that provides IR teams with identity incident response capabilities in a single, easily deployed solution. Silverfort’s Identity IR playbook is mapped to the NIST IR framework’s recommended steps, but we believe the order of these steps needs to be rearranged to be most effective.
The NIST framework divides the IR process into best practices across the following stages:
Preparation
Detection and analysis
Containment, eradication and recovery
Post-incident activity
The most relevant to identity IR is stage 2 (detection and analysis) and stage 3 (containment, eradication and recovery).
NIST emphasizes that IR is not a linear process but a cyclical one, especially between the second and third stages.
This principle is well illustrated when using Silverfort in the IR process. As you’ll soon see, Silverfort’s unique capabilities in MFA and block access in AD environments enable it to perform these stages simultaneously. Let’s see how this is done.
Note that these goals can be achieved using EDR, SIEM, or the standard IR toolkit. However, taking this route entails a long, manual, and error-prone process that takes place while the attack is still in full flow. The purpose of identity IR is to achieve them in a rapid, efficient, and nearly fully automated manner while gaining authentication and user visibility in real time.
Once these goals are achieved, the identity IR merges into the overall IR process to eradicate all malicious presence from the targeted environment.

WHITEPAPER

CISO of a Fortune 100 Company
“Silverfort immediately helped us to mitigate the impact of compromised users. It was one of the most significant tools we used to analyze authentication flow/protocols and determine compromised identities as we brought our Domain Controllers back online. We worked quickly with the IR team to put blocking policies in place over the compromised identities.”
Identity IR refers to all identity-related TTPs, including credential access, privilege escalation, and lateral movement. It complements the existing IR practices that address parallel attack manifestations, such as malware and malicious network traffic, to enhance and accelerate the overall response process.
An organization’s Incident Response Plan (IRP) is the set of processes followed by security teams to respond to an attack. It usually includes detecting the attack’s scope, containing it to prevent further spread, and eradicating adversarial presence and activities.
While there’s an established IR playbook to handle the malware and network aspects of cyberattacks, the identity aspect is lacking. There are no common procedures to identify compromised user accounts and prevent attackers from using them to spread within the targeted environment rapidly and efficiently.
This whitepaper fills this gap by providing an identity IR playbook using Silverfort’s identity security platform. It encloses the aggregated experience of multiple customers who have used it to expedite and optimize their IR processes.
Silverfort policy enforces MFA to all accounts and resources

