
White Paper

The assessment also uncovers any security hygiene issues that can expose the environment to identity threats while detecting any active ones already underway. With this information in hand, organizations can easily identify the identity security gaps preventing them from aligning with insurers’ requirements, so they can resolve them and get the cyber insurance policy they need.
The most stringent requirement put in place by insurers is to apply MFA protection on all administrative access across various resources in the environment, including directory services, networking infrastructure, and command-line access.
Silverfort’s assessment provides complete visibility into all admin users (including shadow admins you might not be aware of) and the resources they access, enabling you to easily see their existing level of MFA cyber insurance coverage and – in the case of any gaps – extend this protection to all necessary users and resources.
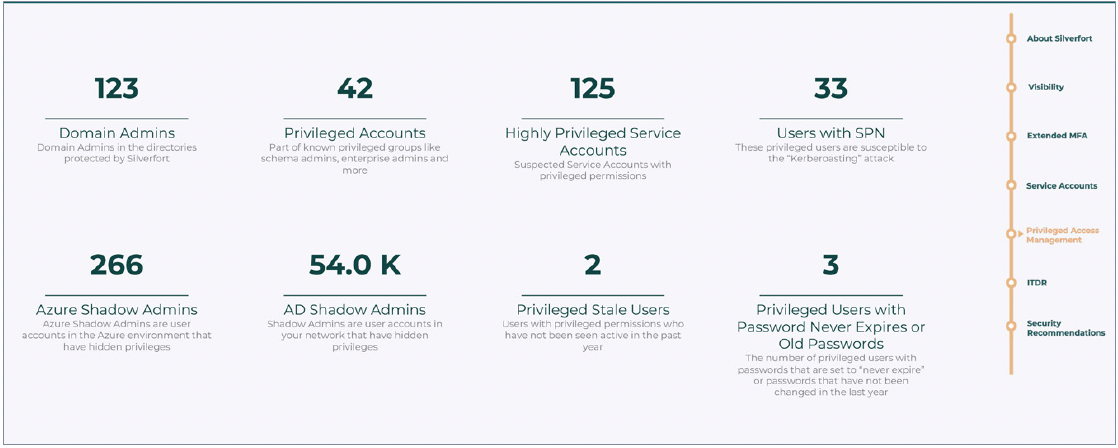
Findings 1: Admin and privileged users visibility
Another important aspect of cyber insurance eligibility is being able to demonstrate that you can monitor and protect your service accounts. Silverfort’s assessment provides you with a complete service account inventory while showing you their privilege levels, source and destination, and the overall activity of each account. Most importantly, this assessment enables you to determine whether any of these accounts are at risk or behaving in an anomalous way that could indicate compromise.
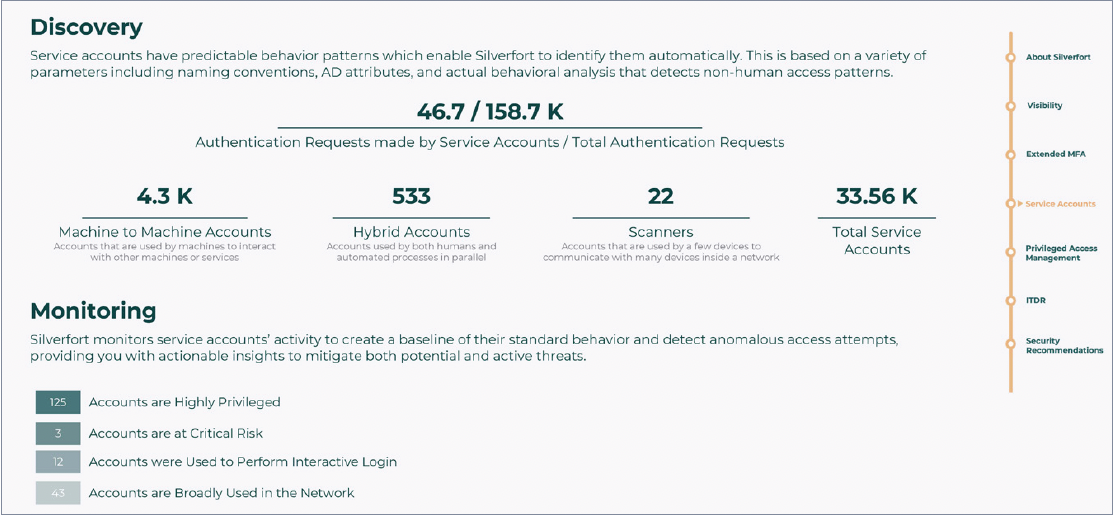
Findings 2: Service account discovery
Silverfort’s assessment tool can also identify security weaknesses in your environment that reduce its resilience to identity threats and expose it to various attack methods. Examples of these include stale passwords in use, accounts with passwords that never expire, admin users with SPN (making them vulnerable to Kerberoasting attacks), as well as the use of any weak protocols like NTLM and NTLMv1. Resolving these hygiene issues is a key step in reducing a threat actor’s ability to attack your environment.
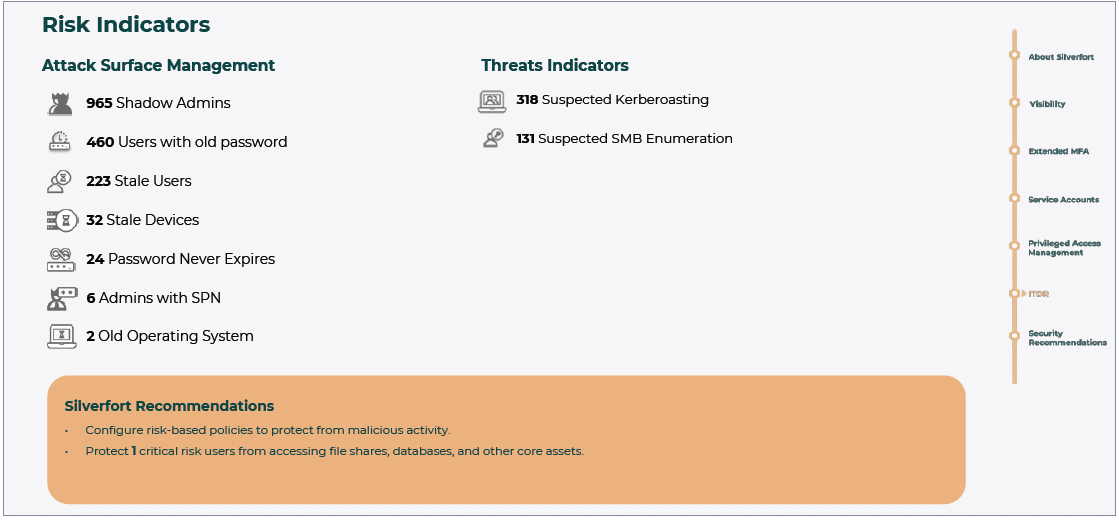
Findings 3: Identity security hygiene
Silverfort’s risk assessment can also spot any live identity threats active in the environment at the time of the assessment. These include common lateral movement techniques (Pass-the-Ticket, Pass-the-Hash, etc.), credential capture such as Kerberoasting, brute force attempts, and others that involve the compromise and use of credentials for malicious access. These techniques enable ransomware actors to spread within a targeted environment and escalate the impact of their attacks from a single machine to an entire network.

Findings 4: Identity Threat Detection & Response (ITDR)
Complying with all new requirements for a cyber insurance policy can be a challenge, especially if you don’t have full visibility into your environment. Thanks to Silverfort’s free identity risk assessment, organizations can meet this challenge head-on. Uncover your security gaps, qualify for cyber insurance, and eliminate the threat of ransomware.
Silverfort secures every dimension of identity. We are the first to deliver end-to-end identity security across the entire IAM infrastructure, eliminating gaps and blind spots, giving businesses visibility into their identity fabric and extending protection to resources that previously could not be protected. This is all done via a patented technology that natively integrates with your entire IAM infrastructure, Runtime Access Protection™ (RAP). It is lightweight, easy to use and deploy, and won’t disrupt business operations, resulting in better security outcomes with less work. Discover every identity across every environment, analyze exposures to reduce your attack surface, and enforce security controls inline to stop lateral movement, ransomware propagation, and other identity threats.
To learn more, visit www.silverfort.com

Silverfort secures every dimension of identity. We are the first to deliver end-to-end identity security across the entire IAM infrastructure, eliminating gaps and blind spots, giving businesses visibility into their identity fabric and extending protection to resources that previously could not be protected. This is all done via a patented technology that natively integrates with your entire IAM infrastructure, Runtime Access Protection™ (RAP). It is lightweight, easy to use and deploy, and won’t disrupt business operations, resulting in better security outcomes with less work. Discover every identity across every environment, analyze exposures to reduce your attack surface, and enforce security controls inline to stop lateral movement, ransomware propagation, and other identity threats.
To learn more, visit www.silverfort.com

White Paper

The assessment also uncovers any security hygiene issues that can expose the environment to identity threats while detecting any active ones already underway. With this information in hand, organizations can easily identify the identity security gaps preventing them from aligning with insurers’ requirements, so they can resolve them and get the cyber insurance policy they need.
The most stringent requirement put in place by insurers is to apply MFA protection on all administrative access across various resources in the environment, including directory services, networking infrastructure, and command-line access.
Silverfort’s assessment provides complete visibility into all admin users (including shadow admins you might not be aware of) and the resources they access, enabling you to easily see their existing level of MFA cyber insurance coverage and – in the case of any gaps – extend this protection to all necessary users and resources.
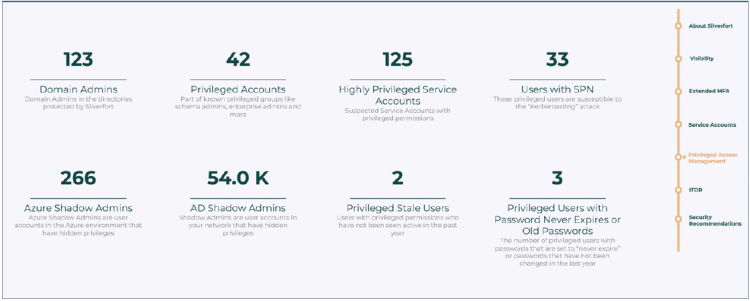
Findings 1: Admin and privileged users visibility
Another important aspect of cyber insurance eligibility is being able to demonstrate that you can monitor and protect your service accounts. Silverfort’s assessment provides you with a complete service account inventory while showing you their privilege levels, source and destination, and the overall activity of each account. Most importantly, this assessment enables you to determine whether any of these accounts are at risk or behaving in an anomalous way that could indicate compromise.
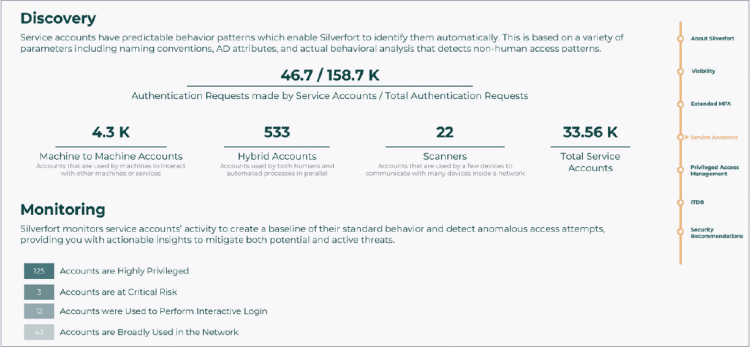
Findings 2: Service account discovery
Silverfort’s assessment tool can also identify security weaknesses in your environment that reduce its resilience to identity threats and expose it to various attack methods. Examples of these include stale passwords in use, accounts with passwords that never expire, admin users with SPN (making them vulnerable to Kerberoasting attacks), as well as the use of any weak protocols like NTLM and NTLMv1. Resolving these hygiene issues is a key step in reducing a threat actor’s ability to attack your environment.
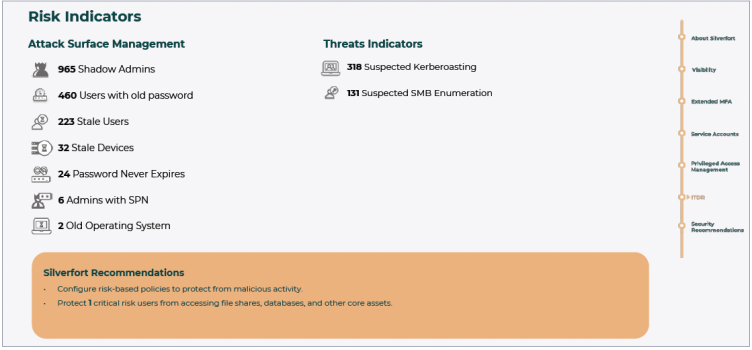
Findings 3: Identity security hygiene
Silverfort’s risk assessment can also spot any live identity threats active in the environment at the time of the assessment. These include common lateral movement techniques (Pass-the-Ticket, Pass-the-Hash, etc.), credential capture such as Kerberoasting, brute force attempts, and others that involve the compromise and use of credentials for malicious access. These techniques enable ransomware actors to spread within a targeted environment and escalate the impact of their attacks from a single machine to an entire network.

Findings 4: Identity Threat Detection & Response (ITDR)
Complying with all new requirements for a cyber insurance policy can be a challenge, especially if you don’t have full visibility into your environment. Thanks to Silverfort’s free identity risk assessment, organizations can meet this challenge head-on. Uncover your security gaps, qualify for cyber insurance, and eliminate the threat of ransomware.

