3
2
1
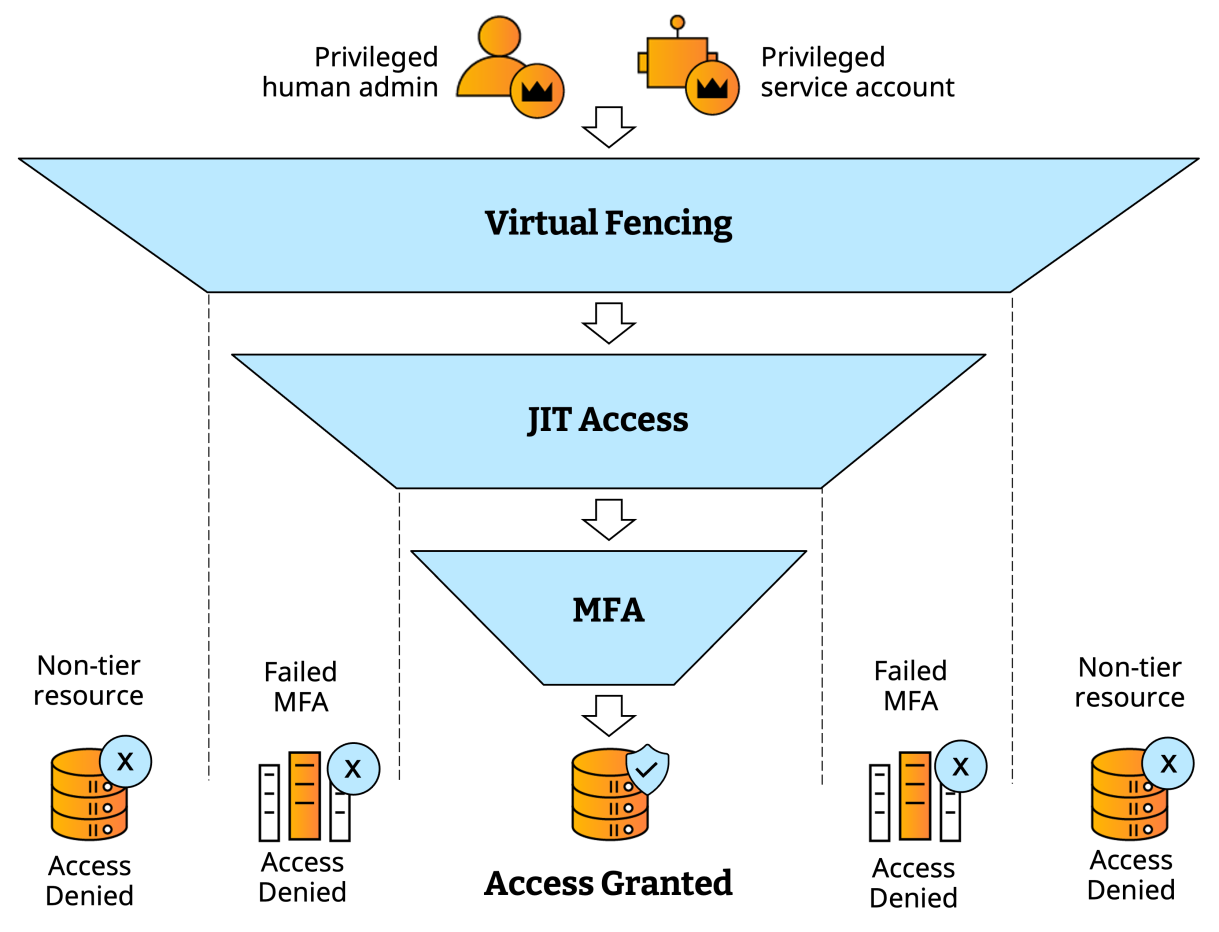
*Layer 2 and 3 (JIT and MFA) naturally apply to human users only, and not to service accounts.
The Silverfort Identity Security Platform enables you to provide a true defense-in-depth protection for the access of privileged users:

Securing Privileged Access: From Blind Spots to Resilience

Silverfort's zero-trust approach to privileged access
Enforce MFA upon access request
Require admins to step up verification upon accessing tiered resources to mitigate the risk of potential credential compromise, extending this protection across every AD access methods including command-line, RDP, and local logins.
3
Layer
Activate accounts per access only with just-in-time access
Apply default disablement of all human users’ administrative accounts, activating them only when an admin submits an access request and provides sufficient justification.
2
Layer
Reduce the attack surface with virtual fencing
Apply least privilege access policies that enable admins to access only resources within their access tier while blocking any attempt to access resources outside of it.
1
Layer
3
2
1
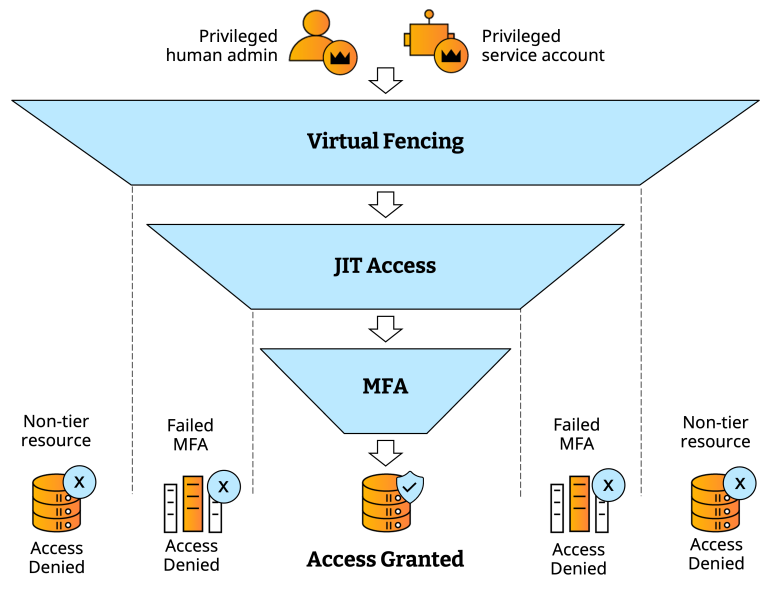
*Layer 2 and 3 (JIT and MFA) naturally apply to human users only, and not to service accounts.
Enforce MFA upon access request
Require admins to step up verification upon accessing tiered resources to mitigate the risk of potential credential compromise, extending this protection across every AD access methods including command-line, RDP, and local logins.
3
Layer
Activate accounts per access only with just-in-time access
Apply default disablement of all human users’ administrative accounts, activating them only when an admin submits an access request and provides sufficient justification.
2
Layer
Reduce the attack surface with virtual fencing
Apply least privilege access policies that enable admins to access only resources within their access tier while blocking any attempt to access resources outside of it.
1
Layer
The Silverfort Identity Security Platform enables you to provide a true defense-in-depth protection for the access of privileged users:

Securing Privileged Access: From Blind Spots to Resilience

Silverfort's zero-trust approach to privileged access