
Silverfort’s Okta Bridge


*A similar flow would apply upon attempting to access any other resource – the only change is the respective directory.
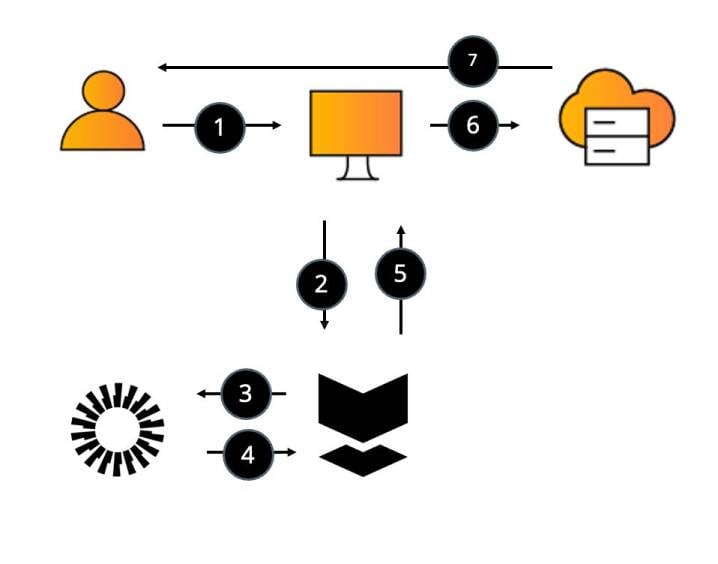
User sends Active Directory (AD) a request to access resource.
AD forwards the request to Silverfort.
Silverfort sends the access request to Okta
Okta evaluates authentication based on its policy and makes a verdict if to allow/MFA or block.
Okta forwards the verdict to Silverfort.
Silverfort accepts the verdict and forwards it to AD.
AD sends the response to the user to either allow the authentication or block it.
Silverfort's Okta Bridge enables organizations to implement Okta web SSO flows to on-prem applications within their Okta environment and apply security controls to these resources. This enables enterprises to gain real-time protection against identity-based attacks that utilize compromised credentials to access enterprise on-prem or cloud resources. Silverfort bridge allows organizations to extend authentications with Okta, enabling better visibility into their users' and resources' activities across web and on prem applications.
Bridging Legacy Resources
Okta's security controls can be extended using Silverfort bridging, while access policies can be applied to any resource on-prem or in multi-cloud environments. This enables organizations to apply strong modern identity security controls to all resources. By enforcing new security measures with Silverfort, organizations can take proactive measures against incoming cyber threats such as lateral movement attacks.
How Does Silverfort’s Okta Bridge Work
Silverfort can seamlessly bridge any type of application authentication (legacy apps, command-line tools, and more) into Okta as if it were a modern web application. With Silverfort's Okta bridge, customers can create applications representing the on-prem resource in Okta. Okta views this object as a SaaS app like any other cloud-based application. In Okta, configure an access policy for the application object that can utilize Okta Adaptive Authentication and MFA. By creating and applying the policy to each bridged on-prem resource, organizations will consolidate hybrid resources. Once the authentication and access policies have been configured, Silverfort monitors and protects attempts to access resources. All bridged applications can now be managed, monitored, and protected in Okta.
Protect the
‘Unprotectable’
Extend Okta MFA and access policies to any resource, including on-prem servers, legacy apps, IT infrastructure, and command-line tools.
Unified Policy Enforcement
Secure on-prem environments and resources with Okta policies via Silverfort, reducing identity-based risks.
Seamless User Experience
Provide users with a consistent and familiar experience when accessing any resource, both on-prem and in the cloud.
Hybrid Attack Protection
Detect and prevent advanced lateral movement attacks that traverse between the on-prem and cloud environments.


Silverfort’s Okta Bridge

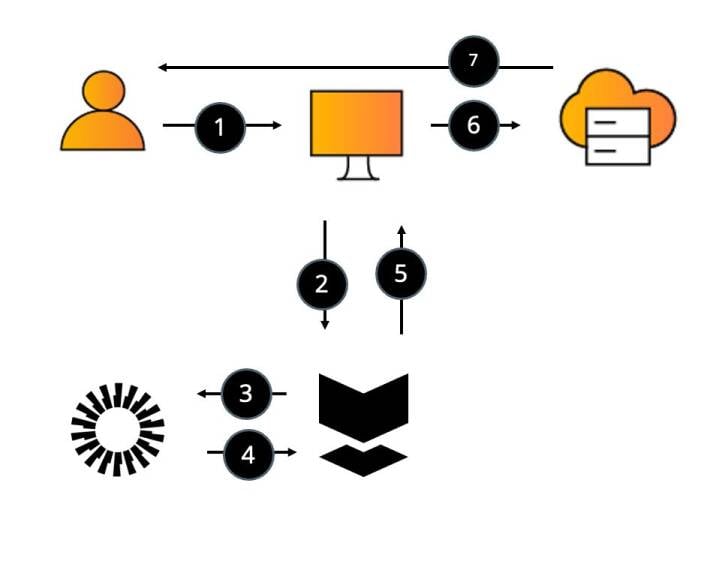
User sends Active Directory (AD) a request to access resource.
AD forwards the request to Silverfort.
Silverfort sends the access request to Okta
Okta evaluates authentication based on its policy and makes a verdict if to allow/MFA or block.
Okta forwards the verdict to Silverfort.
Silverfort accepts the verdict and forwards it to AD.
AD sends the response to the user to either allow the authentication or block it.
*A similar flow would apply upon attempting to access any other resource – the only change is the respective directory.
Silverfort's Okta Bridge enables organizations to implement Okta web SSO flows to on-prem applications within their Okta environment and apply security controls to these resources. This enables enterprises to gain real-time protection against identity-based attacks that utilize compromised credentials to access enterprise on-prem or cloud resources. Silverfort bridge allows organizations to extend authentications with Okta, enabling better visibility into their users' and resources' activities across web and on prem applications.
Bridging Legacy Resources
Okta's security controls can be extended using Silverfort bridging, while access policies can be applied to any resource on-prem or in multi-cloud environments. This enables organizations to apply strong modern identity security controls to all resources. By enforcing new security measures with Silverfort, organizations can take proactive measures against incoming cyber threats such as lateral movement attacks.
How Does Silverfort’s Okta Bridge Work
Silverfort can seamlessly bridge any type of application authentication (legacy apps, command-line tools, and more) into Okta as if it were a modern web application. With Silverfort's Okta bridge, customers can create applications representing the on-prem resource in Okta. Okta views this object as a SaaS app like any other cloud-based application. In Okta, configure an access policy for the application object that can utilize Okta Adaptive Authentication and MFA. By creating and applying the policy to each bridged on-prem resource, organizations will consolidate hybrid resources. Once the authentication and access policies have been configured, Silverfort monitors and protects attempts to access resources. All bridged applications can now be managed, monitored, and protected in Okta.
Protect the ‘Unprotectable’
Extend Okta MFA and access policies to any resource, including on-prem servers, legacy apps, IT infrastructure, and command-line tools.
Unified Policy Enforcement
Secure on-prem environments and resources with Okta policies via Silverfort, reducing identity-based risks.
Seamless User Experience
Provide users with a consistent and familiar experience when accessing any resource, both on-prem and in the cloud.
Hybrid Attack Protection
Detect and prevent advanced lateral movement attacks that traverse between the on-prem and cloud environments.

