
NHI Security
Has Never Been Easier


Silverfort leverages its native integration with the on-prem and cloud IAM infrastructure to identify the NHI accounts based on their repetitive and pattern-like behavior.
Once Silverfort validates an account as an NHI it maps its baseline activity and auto-creates an access policy that places a virtual fence around the account, allowing it to access its baseline destinations only.
When activated, this policy would disable adversaries' ability to use the compromised account for lateral movement since every anomalous access will ne blocked.
Effortless Scale
Group all the accounts you want to protect under a single policy, continue adding accounts until all are protected, and integrate with your app management tool for easy operation

Automated Discovery
Gain visibility into all NHI inventory, Including the name, privilege level, security posture, sources, and destinations of every account so you can prioritize the ones to protect..

Real-Time Protection
Activate an auto-generated policy that allows the account to access its standard sources and destinations, and triggers access block or alert upon detecting a deviation.
Of the lateral movement attacks investigated by Silverfort researchers have involved the compromise and use of an NHI, most notably an Active Directory service account.
NHI, especially in Active Directory environment are a highly exposed and targeted attack surface, due to the following reasons:
Low visibility level, with many active NHI operating without being known to the IAM and security teams,
High access privileges to multiple resources in order to manage the services they are accountable for.
They can't be protected with MFA because they're not human, and are hard to protect PAM password rotation due to operational disruption concerns.
Silverfort is the first solution to automate the full NHI protection, making thus critical need, finally within every organization's reach.
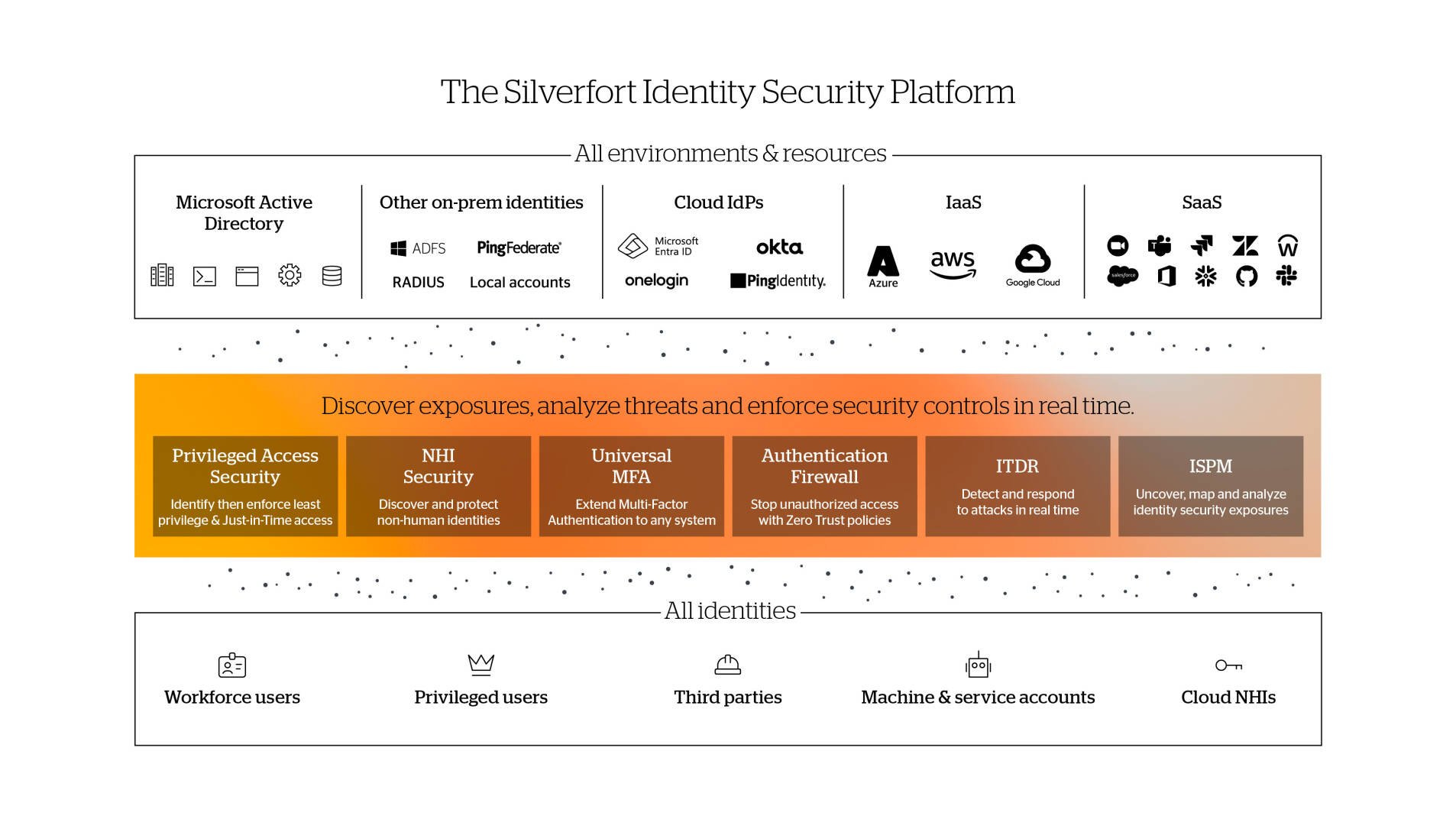
NHI security plays a key part in Silverfort’s task to deliver comprehensive identity, that is mitigate the risk of malicious access with compromised credentials.
Silverfort identity security platform achieves that with its three core capabilities:
Continuous discovery of every user account and its activities within the hybrid environment.
Risk analysis of accounts security posture, and of every authentication and access attempt.
Real-time enforcement to block unauthorised and malicious access.
Silverfort implements these capabilities across all users, resources, and on-prem and cloud environments, enabling organizations to secure their entire identity attack surface with a single solution, easy to deploy and manages
About Silverfort
Finally, the identity security platform you deserve. Silverfort connects to your entire infrastructure to protect it from within. By breaking down silos and eliminating blind spots, Silverfort is the first to give businesses visibility into their whole network of identities and secure every identity, every resource, and every environment—all the time.

NHI Security
Has Never Been Easier

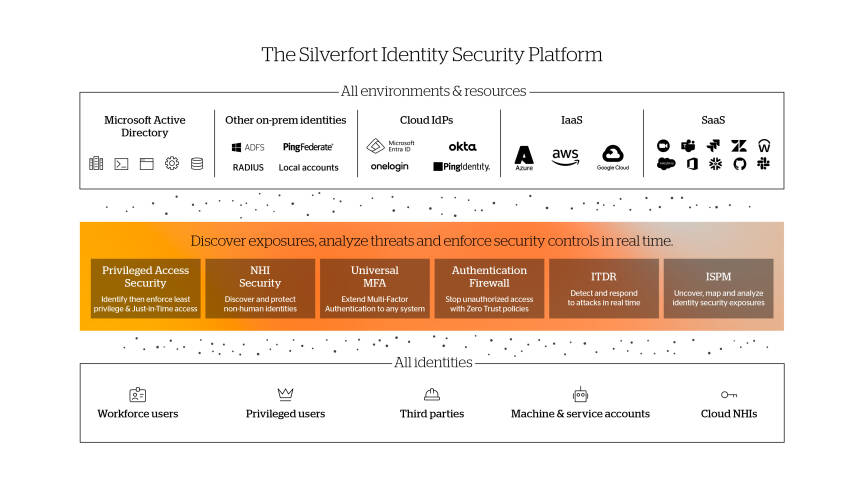
NHI security plays a key part in Silverfort’s task to deliver comprehensive identity, that is mitigate the risk of malicious access with compromised credentials.
Silverfort identity security platform achieves that with its three core capabilities:
Continuous discovery of every user account and its activities within the hybrid environment.
Risk analysis of accounts security posture, and of every authentication and access attempt.
Real-time enforcement to block unauthorised and malicious access.
Silverfort implements these capabilities across all users, resources, and on-prem and cloud environments, enabling organizations to secure their entire identity attack surface with a single solution, easy to deploy and manages
About Silverfort
Finally, the identity security platform you deserve. Silverfort connects to your entire infrastructure to protect it from within. By breaking down silos and eliminating blind spots, Silverfort is the first to give businesses visibility into their whole network of identities and secure every identity, every resource, and every environment—all the time.
Of the lateral movement attacks investigated by Silverfort researchers have involved the compromise and use of an NHI, most notably an Active Directory service account.
NHI, especially in Active Directory environment are a highly exposed and targeted attack surface, due to the following reasons:
Low visibility level, with many active NHI operating without being known to the IAM and security teams,
High access privileges to multiple resources in order to manage the services they are accountable for.
They can't be protected with MFA because they're not human, and are hard to protect PAM password rotation due to operational disruption concerns.
Silverfort is the first solution to automate the full NHI protection, making thus critical need, finally within every organization's reach.

Silverfort leverages its native integration with the on-prem and cloud IAM infrastructure to identify the NHI accounts based on their repetitive and pattern-like behavior.
Once Silverfort validates an account as an NHI it maps its baseline activity and auto-creates an access policy that places a virtual fence around the account, allowing it to access its baseline destinations only.
When activated, this policy would disable adversaries' ability to use the compromised account for lateral movement since every anomalous access will ne blocked.
Zero manual effort for real-time protection
Effortless Scale
Group all the accounts you want to protect under a single policy, continue adding accounts until all are protected, and integrate with your app management tool for easy operation

Real-Time Protection
Activate an auto-generated policy that allows the account to access its standard sources and destinations, and triggers access block or alert upon detecting a deviation.

Automated Discovery
Gain visibility into all NHI inventory, Including the name, privilege level, security posture, sources, and destinations of every account so you can prioritize the ones to protect..

