
Identity Security
Posture Management (ISPM)

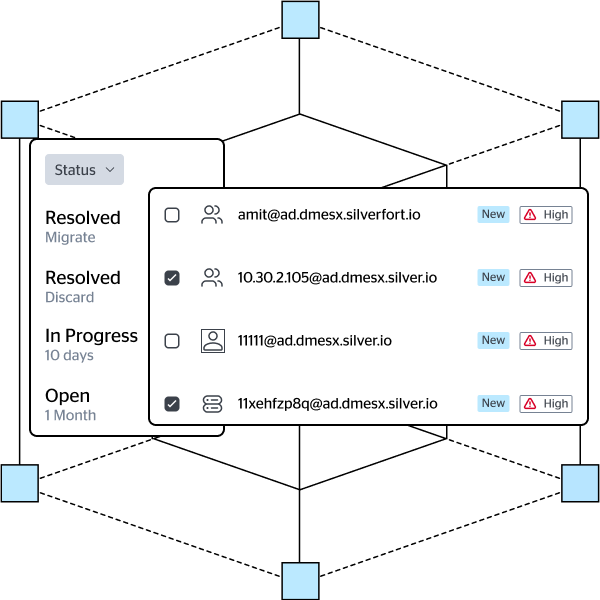
Silverfort leverages its patented Runtime Access Protection (RAP) technology to provide you with full visibility to any identity weakness that adveraries might target to perform credential access, privilege escalation and lateral movement.
By proactively detecting and resolving threat exposures such as shadow admins, NTLMv1 usage, stale users, and many others, you’re placing critical barriers in attacker’s TTPs. This investment in building up your identity security posture, returns immediate investment as attackers will move away from your environment in search for more vulnerable targets.
User and Authentication Hygiene
Pinpoint operational issues such as failed authentication, stale accounts, on-prem accounts that were accidentally synced to the cloud and many more.

IAM Hardening
Resolve any detected issue in your AD, cloud IdP, or federation infrastructure by continuously monitoring their resilience to the widest range of identity threats.
Threat Exposure Management
Discover Identity Threat Exposures that allow adversaries to perform credential access, privilege escalation, and lateral movement
of data breaches involve the use of compromised credentials. This would entail a prepatroty credential access which would often follow with privilege escalation. The combined impact of these tactics is he X factor that turns a local security event into an enterprise-level breach. Stay ahead of the curve and make sure that your environment is resilient.
More than any attack surface, identity is the most prone to human errors that result in increased exposure. Silverfort provides throws a spotlight on all the weaknesses that are common to all environments, enabling you to immune your environments and attackers’ identity threat playbook.
While investigating ab active breach requires dedicated skills, time, and resources, adjusting user accounts’ configuratio, removing excessive permissions, and reverting from malpractices is easily within reach. Silverfort ISPM is your ultimate companion in this journey, eliminating your knowledge blind spot and guiding you directly to the user accounts that need to be fixed.
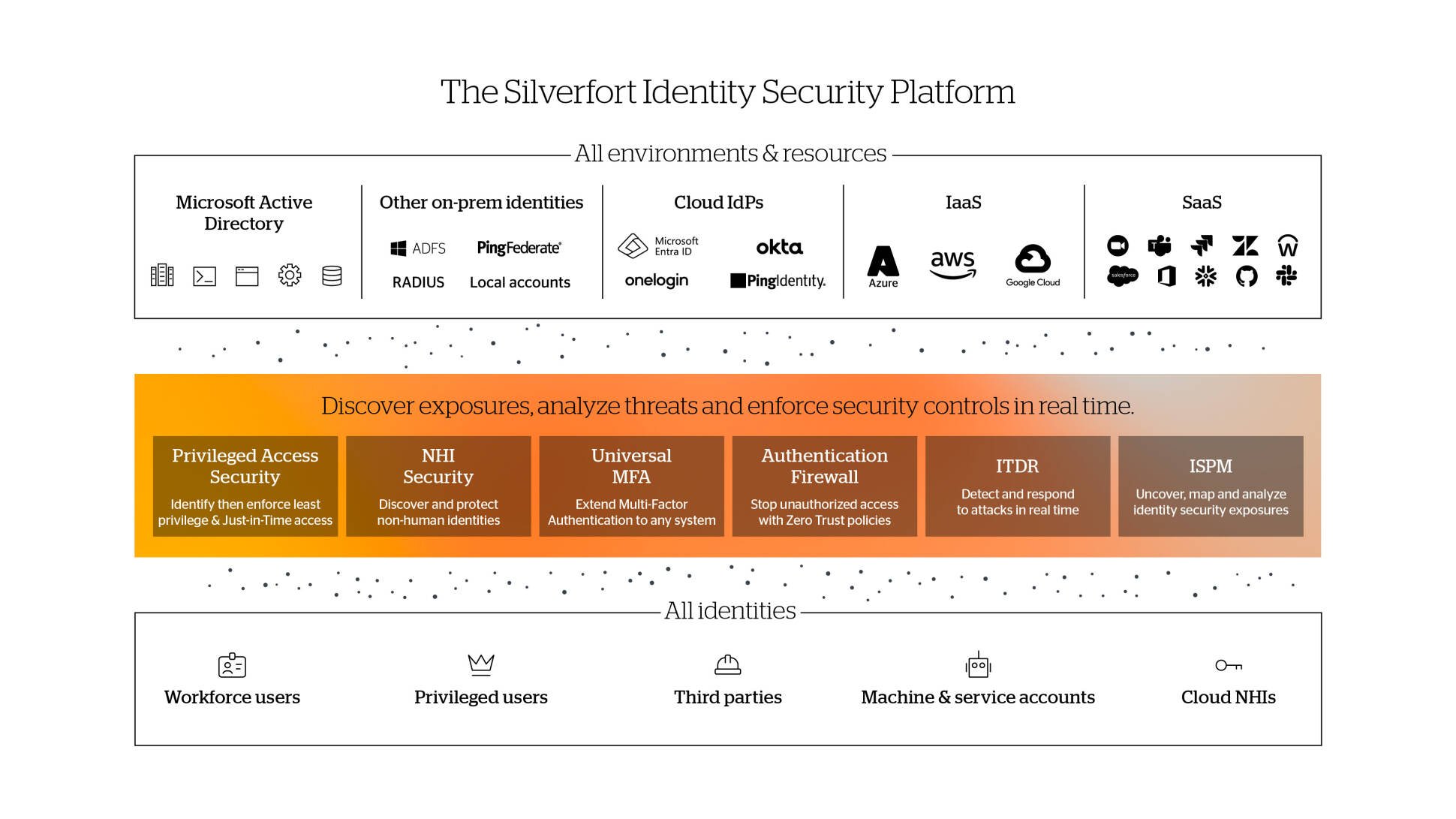
ISPM plays a key part in Silverfort’s task to deliver comprehensive identity, that is mitigate the risk of malicious access with compromised credentials.
Silverfort identity security platform achieves that with its three core capabilities:
Continuous discovery of every user account and its activities within the hybrid environment.
Risk analysis of accounts security posture, and of every authentication and access attempt.
Real-time enforcement to block unauthorised and malicious access.
Silverfort implements these capabilities across all users, resources, and on-prem and cloud environments, enabling organizations to secure their entire identity attack surface with a single solution, easy to deploy and manages
About Silverfort
Finally, the identity security platform you deserve. Silverfort connects to your entire infrastructure to protect it from within. By breaking down silos and eliminating blind spots, Silverfort is the first to give businesses visibility into their whole network of identities and secure every identity, every resource, and every environment—all the time.

Identity Security
Posture Management (ISPM)

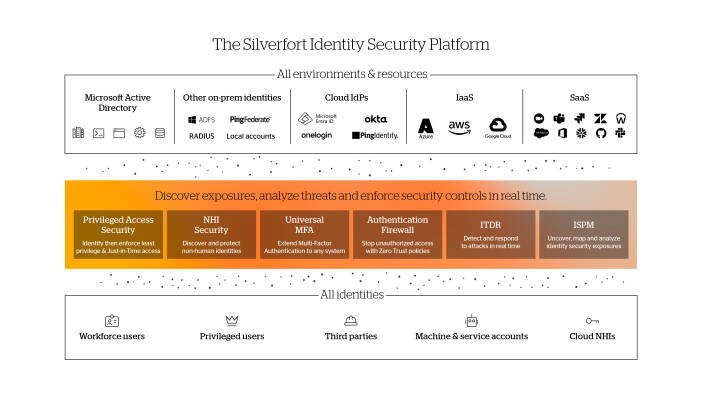
ISPM plays a key part in Silverfort’s task to deliver comprehensive identity, that is mitigate the risk of malicious access with compromised credentials.
Silverfort identity security platform achieves that with its three core capabilities:
Continuous discovery of every user account and its activities within the hybrid environment.
Risk analysis of accounts security posture, and of every authentication and access attempt.
Real-time enforcement to block unauthorised and malicious access.
Silverfort implements these capabilities across all users, resources, and on-prem and cloud environments, enabling organizations to secure their entire identity attack surface with a single solution, easy to deploy and manages
About Silverfort
Finally, the identity security platform you deserve. Silverfort connects to your entire infrastructure to protect it from within. By breaking down silos and eliminating blind spots, Silverfort is the first to give businesses visibility into their whole network of identities and secure every identity, every resource, and every environment—all the time.
of data breaches involve the use of compromised credentials. This would entail a prepatroty credential access which would often follow with privilege escalation. The combined impact of these tactics is he X factor that turns a local security event into an enterprise-level breach. Stay ahead of the curve and make sure that your environment is resilient.
More than any attack surface, identity is the most prone to human errors that result in increased exposure. Silverfort provides throws a spotlight on all the weaknesses that are common to all environments, enabling you to immune your environments and attackers’ identity threat playbook.
While investigating ab active breach requires dedicated skills, time, and resources, adjusting user accounts’ configuratio, removing excessive permissions, and reverting from malpractices is easily within reach. Silverfort ISPM is your ultimate companion in this journey, eliminating your knowledge blind spot and guiding you directly to the user accounts that need to be fixed.
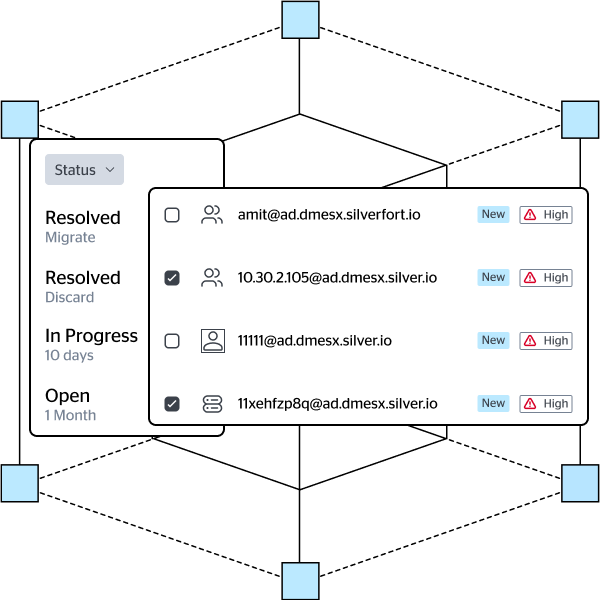
Silverfort leverages its patented Runtime Access Protection (RAP) technology to provide you with full visibility to any identity weakness that adveraries might target to perform credential access, privilege escalation and lateral movement.
By proactively detecting and resolving threat exposures such as shadow admins, NTLMv1 usage, stale users, and many others, you’re placing critical barriers in attacker’s TTPs. This investment in building up your identity security posture, returns immediate investment as attackers will move away from your environment in search for more vulnerable targets.
An ounce of prevention is worth a pound of cure
User and Authentication Hygiene
Pinpoint operational issues such as failed authentication, stale accounts, on-prem accounts that were accidentally synced to the cloud and many more.

IAM Hardening
Resolve any detected issue in your AD, cloud IdP, or federation infrastructure by continuously monitoring their resilience to the widest range of identity threats.
Threat Exposure Management
Discover Identity Threat Exposures that allow adversaries to perform credential access, privilege escalation, and lateral movement

