
Authentication Firewall
The Power of Deny

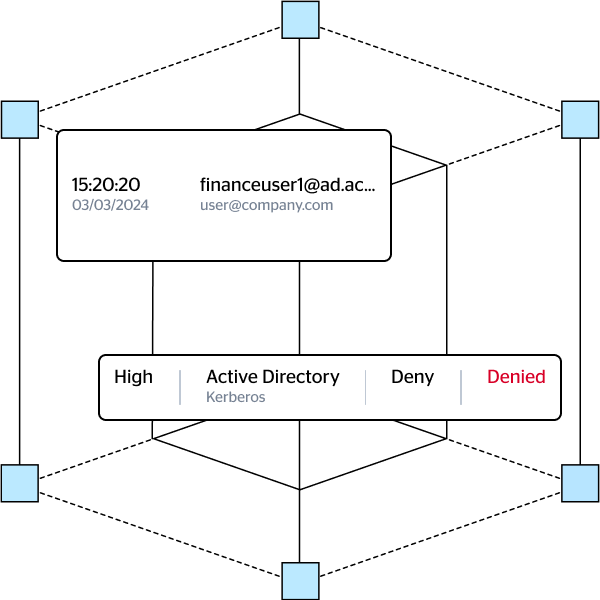
Silverfort leverages its patented Runtime Access Protection (RAP) technology to govern and control user access in the hybrid environment, and provide access policies that are far more granular and flexible than ones configured in the undelying IAM solution.
The authentication firewall’s policies can be implemented seamlessly and rapidly, activated or disabled in a single click. These policies can serve a wide range of purposes, such as eliminating the use of legacy protocols, enforcing least privileged access policies, or contain active attacks by revoking all user access.

Rapid Incident Response
Contain detected attacks with a single click by blocking any attempted malicious access, halting the attack’s progression.
Identity Segmentation
Enforce least privileged access policies on your workforce, ensuring users only access the resources they truly need and removing any excessive access permissions.
Attack Surface Reduction
Increase your environment’s identity threats resilience by eliminating the use of insecure protocols such as NTLMv1 and cleartext LDAP, and other risky authentications.
of data breaches involve the use of compromised credentials for lateral movement. This makes the ability to block the spread of detected attacks a critical need for every organization.
Authentication firewall is the best option to manage users' access in your AD environment. Too often, AD access policies are either to crude or too complicated to enable efficient control on users' secure access.
The high flexibility of the authentication firewall interface ensures that IAM teams can easily and accurately impllement theur secure access strategy of choice:
User accounts: can be configured based on their individual identity, their AD group, or a combination of both.
Source anc destination resources: can also be configured based on their indivicual identity, their AD group, or a combination of both.
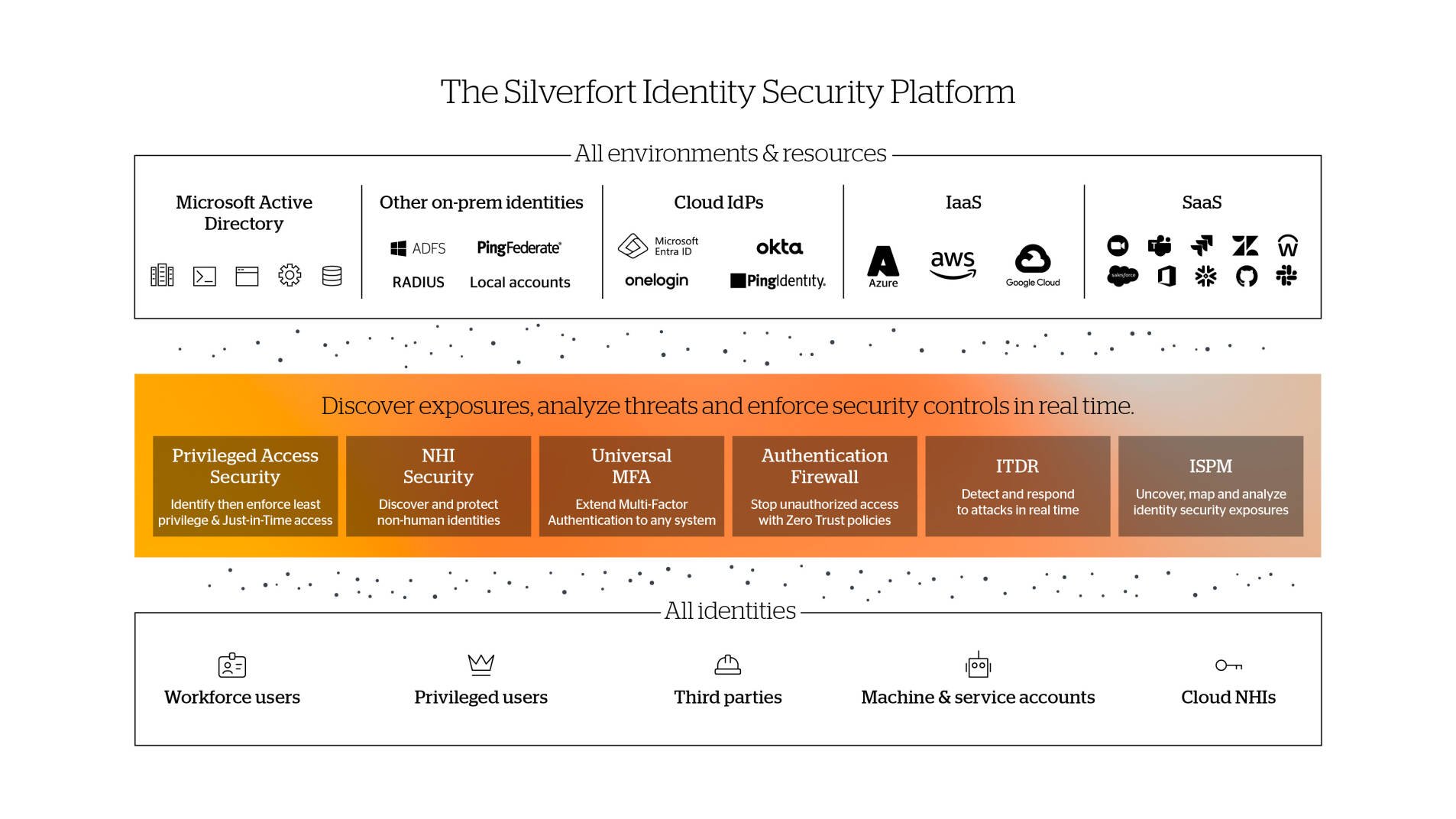
Authentication firewall plays a key part in Silverfort’s task to deliver comprehensive identity, that is mitigate the risk of malicious access with compromised credentials.
Silverfort identity security platform achieves that with its three core capalities:
Continuous discovery of every user account in the enterprise environment,
Risk analysis of accounts security posture, and of every authentication and access attempt.
Real-time enforcement to block unauthorised and malicious access.
Silverfort implements these capabilities across all users, resources, and on-prem and cloud environments, enabling organizations to secure their entire identity attack surface with a single solution, easy to deploy and manages.
About Silverfort
Finally, the identity security platform you deserve. Silverfort connects to your entire infrastructure to protect it from within. By breaking down silos and eliminating blind spots, Silverfort is the first to give businesses visibility into their whole network of identities and secure every identity, every resource, and every environment—all the time.

Authentication Firewall
The Power of Deny

Authentication firewall plays a key part in Silverfort’s task to deliver comprehensive identity, that is mitigate the risk of malicious access with compromised credentials.
Silverfort identity security platform achieves that with its three core capalities:
Continuous discovery of every user account in the enterprise environment,
Risk analysis of accounts security posture, and of every authentication and access attempt.
Real-time enforcement to block unauthorised and malicious access.
Silverfort implements these capabilities across all users, resources, and on-prem and cloud environments, enabling organizations to secure their entire identity attack surface with a single solution, easy to deploy and manages.
About Silverfort
Finally, the identity security platform you deserve. Silverfort connects to your entire infrastructure to protect it from within. By breaking down silos and eliminating blind spots, Silverfort is the first to give businesses visibility into their whole network of identities and secure every identity, every resource, and every environment—all the time.
of data breaches involve the use of compromised credentials for lateral movement. This makes the ability to block the spread of detected attacks a critical need for every organization.
Authentication firewall is the best option to manage users' access in your AD environment. Too often, AD access policies are either to crude or too complicated to enable efficient control on users' secure access.
The high flexibility of the authentication firewall interface ensures that IAM teams can easily and accurately impllement theur secure access strategy of choice:
User accounts: can be configured based on their individual identity, their AD group, or a combination of both.
Source anc destination resources: can also be configured based on their indivicual identity, their AD group, or a combination of both.
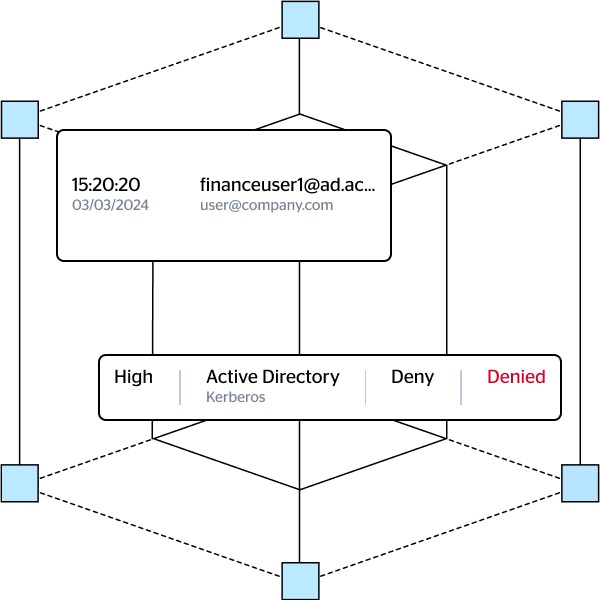
Silverfort leverages its patented Runtime Access Protection (RAP) technology to govern and control user access in the hybrid environment, and provide access policies that are far more granular and flexible than ones configured in the undelying IAM solution.
The authentication firewall’s policies can be implemented seamlessly and rapidly, activated or disabled in a single click. These policies can serve a wide range of purposes, such as eliminating the use of legacy protocols, enforcing least privileged access policies, or contain active attacks by revoking all user access.
Dynamic and flexible interface to govern all user access

Rapid Incident Response
Contain detected attacks with a single click by blocking any attempted malicious access, halting the attack’s progression.

Attack Surface Reduction
Increase your environment’s identity threats resilience by eliminating the use of insecure protocols such as NTLMv1 and cleartext LDAP, and other risky authentications.
Identity Segmentation
Enforce least privileged access policies on your workforce, ensuring users only access the resources they truly need and removing any excessive access permissions.

