THEY'RE UNDER-OBSERVED

The silent risk: How non-human identities open the door to cyber threats

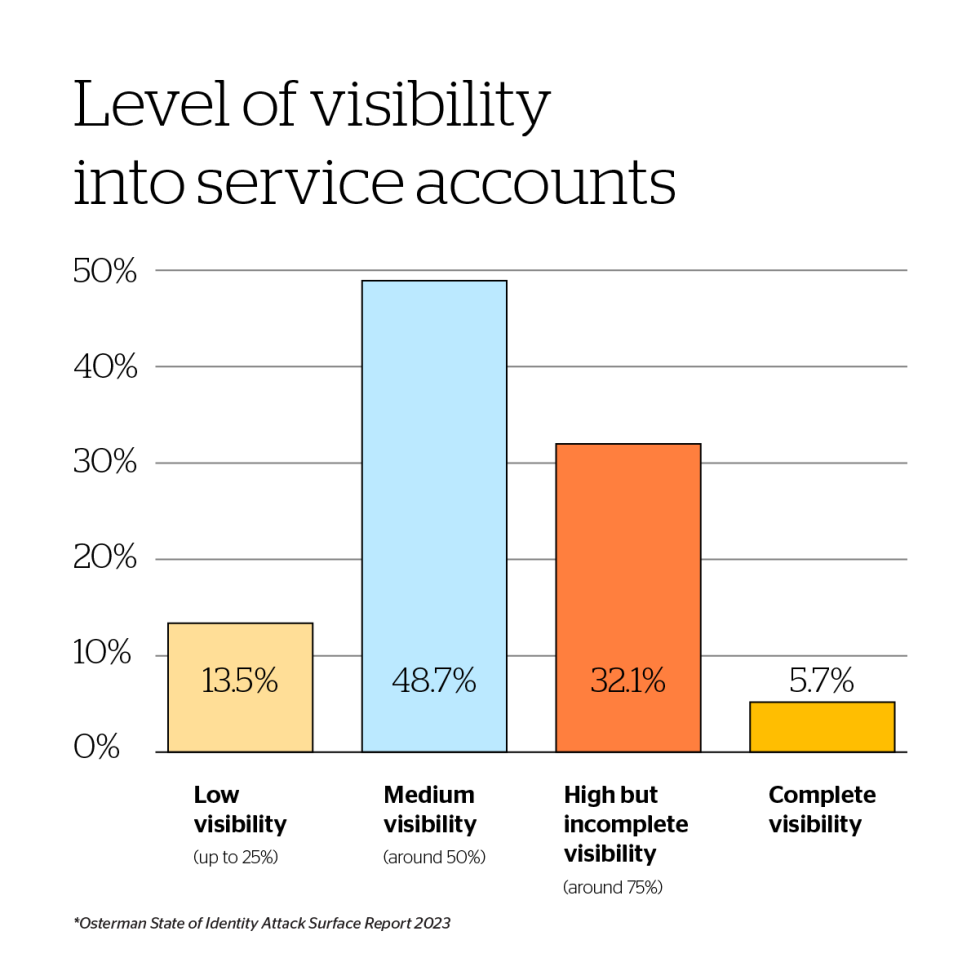
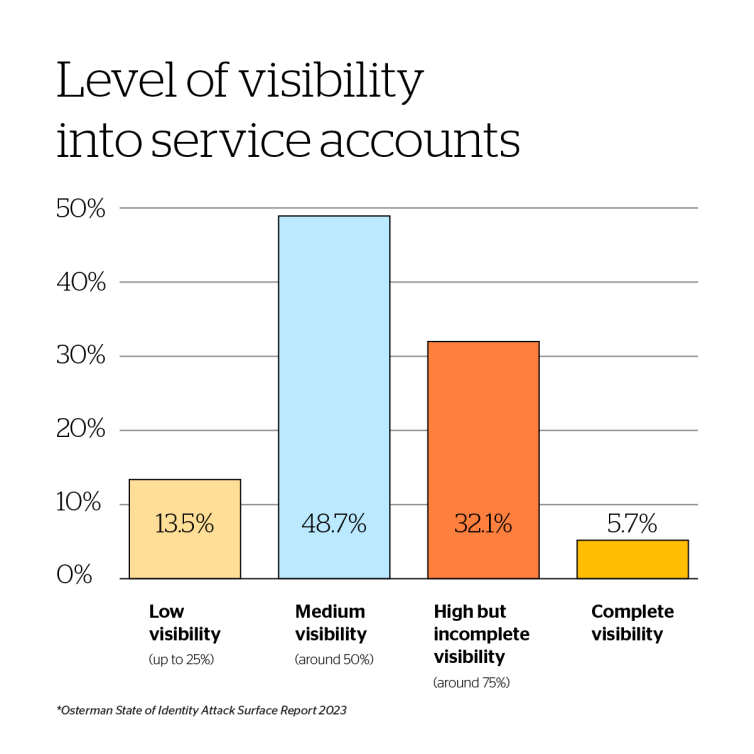
Most organizations don’t have full visibility into their NHIs. In fact, only 5.7% of security leaders believe they know where all their NHIs are and what they do, making it hard to detect misuse and even harder to secure every single one of them. Within the large pool of NHI types, service accounts — used for machine-to-machine communication within Microsoft’s Active Directory’s (AD) environments — are very concerning. Our data shows that on average 35% of a company’s user accounts are service accounts.
It began with human admins creating NHIs across multiple systems, apps, platforms and services without a centralized view of what they are responsible for, who created and owns them, and what they need access to. For most organizations, there has never been a single source of truth for NHIs, nor any standardized onboarding, offboarding, or ownership processes, leaving their inventories incomplete at best.
The shift to the cloud exacerbated this issue—and set the stage for Gen AI, Large Language Models (LLMs) and Copilot to autonomously and silently use NHIs.
Without ongoing visibility into what is being created and why, organizations are forced to play catchup to their growing identity attack surface. After all, you can’t protect what you can’t see.
NHIs are easy to create but difficult to monitor

The silent risk: How non-human identities open the door to cyber threats

Most organizations don’t have full visibility into their NHIs. In fact, only 5.7% of security leaders believe they know where all their NHIs are and what they do, making it hard to detect misuse and even harder to secure every single one of them. Within the large pool of NHI types, service accounts — used for machine-to-machine communication within Microsoft’s Active Directory’s (AD) environments — are very concerning. Our data shows that on average 35% of a company’s user accounts are service accounts
It began with human admins creating NHIs across multiple systems, apps, platforms and services without a centralized view of what they are responsible for, who created and owns them, and what they need access to. For most organizations, there has never been a single source of truth for NHIs, nor any standardized onboarding, offboarding, or ownership processes, leaving their inventories incomplete at best.
The shift to the cloud exacerbated this issue—and set the stage for Gen AI, Large Language Models (LLMs) and Copilot to autonomously and silently use NHIs.
Without ongoing visibility into what is being created and why, organizations are forced to play catchup to their growing identity attack surface. After all, you can’t protect what you can’t see.
NHIs are easy to create but difficult to monitor