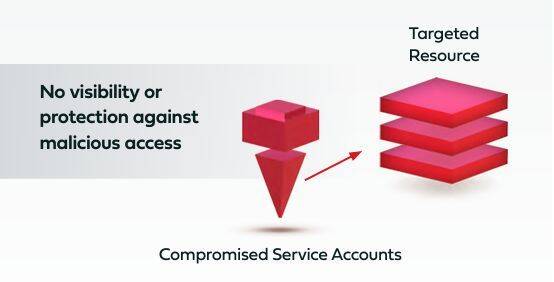



Overcoming the Security Blind Spot of Service Accounts


Identity security platform
How: Automated discovery, monitoring and protection for all service accounts.
Pros: Full coverage, zero manual effort, automated blocking of malicious activity.
Cons: Need to manually enable policies.

Manual discovery and monitoring
How: Investigating directories and machines to identify service accounts and their associated scripts.
Pros: Does not require a dedicated solution
or skill.Cons: Resource consuming, partial results, prone to human error.

Alerting on anomalous activity
How: Utilizing Security Information and Event Management (SIEM) or Endpoint Detection and Response (EDR) platforms to alert when deviations from normal behavior occur.
Pros: Automated alerting.
Cons: Allows malicious activity to continue while investigation takes place, requires highly skilled security team, prone to alert fatigue.
T he three approaches to protecting Service Accounts


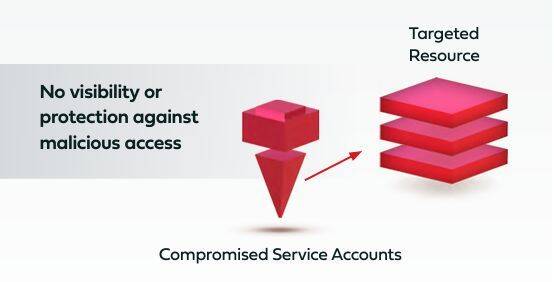
Overcoming the Security Blind Spot of Service Accounts



Identity security platform
How: Automated discovery, monitoring and protection for all service accounts.
Pros: Full coverage, zero manual effort, automated blocking of malicious activity.
Cons: Need to manually enable policies.

Alerting on anomalous activity
How: Utilizing Security Information and Event Management (SIEM) or Endpoint Detection and Response (EDR) platforms to alert when deviations from normal behavior occur.
Pros: Automated alerting.
Cons: Allows malicious activity to continue while investigation takes place, requires highly skilled security team, prone to alert fatigue.

Manual discovery and monitoring
How: Investigating directories and machines to identify service accounts and their associated scripts.
Pros: Does not require a dedicated solution
or skill.Cons: Resource consuming, partial results, prone to human error.
T he three approaches to protecting Service Accounts